
Today, it is imperative for many organizations to have full control of the keys that are used for encrypting their data in the cloud and to be in a position to revoke that access (to the encrypted data) with those keys at any time. To support the customer in this, T-Systems has launched a new product , External Key Management (EKM) as announced in their press release on 30th November 2022.

Encrypting data in the cloud is a fundamental requirement of cloud security. However, using and managing data encryption keys in a public cloud is challenging. Sensitive data encryption and privacy have recently received widespread attention and focus in the IT industry. This can be partially attributed to compliance requirements such in Schrems II rulings and GDPR regulations which have made cloud providers realize that it is incumbent upon them to strive to develop new services and features to address these new data privacy requirements. AWS released at the annual AWS re:Invent 2022 their new solution External Key Store (XKS). This solution was developed after extensive collaboration between experts from AWS, HSM and key management providers, and Managed Cloud Services providers (MCS) such as our T-Systems security team.
External Key Store (XKS) is a new feature introduced by AWS Key Management Service (AWS KMS). It is a custom key store backed by an external key manager outside AWS. This key manager can be any physical or virtual hardware security modules (HSMs), or any hardware-based or software-based system that can be used to generate and store cryptographic keys and perform cryptographic operations such as encrypting and decrypting data. (Here, external key manager refers to any of these concepts). AWS refers to this as Hold Your Own Keys (HYOKs), where two keys are used:
When an AWS service requests data encryption using XKS KMS key, KMS generates a data key, encrypts it with the XKS KMS key and sends it to the external key manager and double encrypt it using the external key. KMS returns:
As the plaintext data key is needed for decryption, the stored double encrypted data key must be decrypted with the external key and then with the XKS KMS key Hence, revoking access to any of those keys will make this double encrypted data key useless, and data decryption impossible. For more information, see External key stores.
T-Systems developed EKM to support customers implementing the AWS External Key Store service while adhering to regulatory security and compliancy measures.
T-Systems EKM value proposition focuses on three areas:
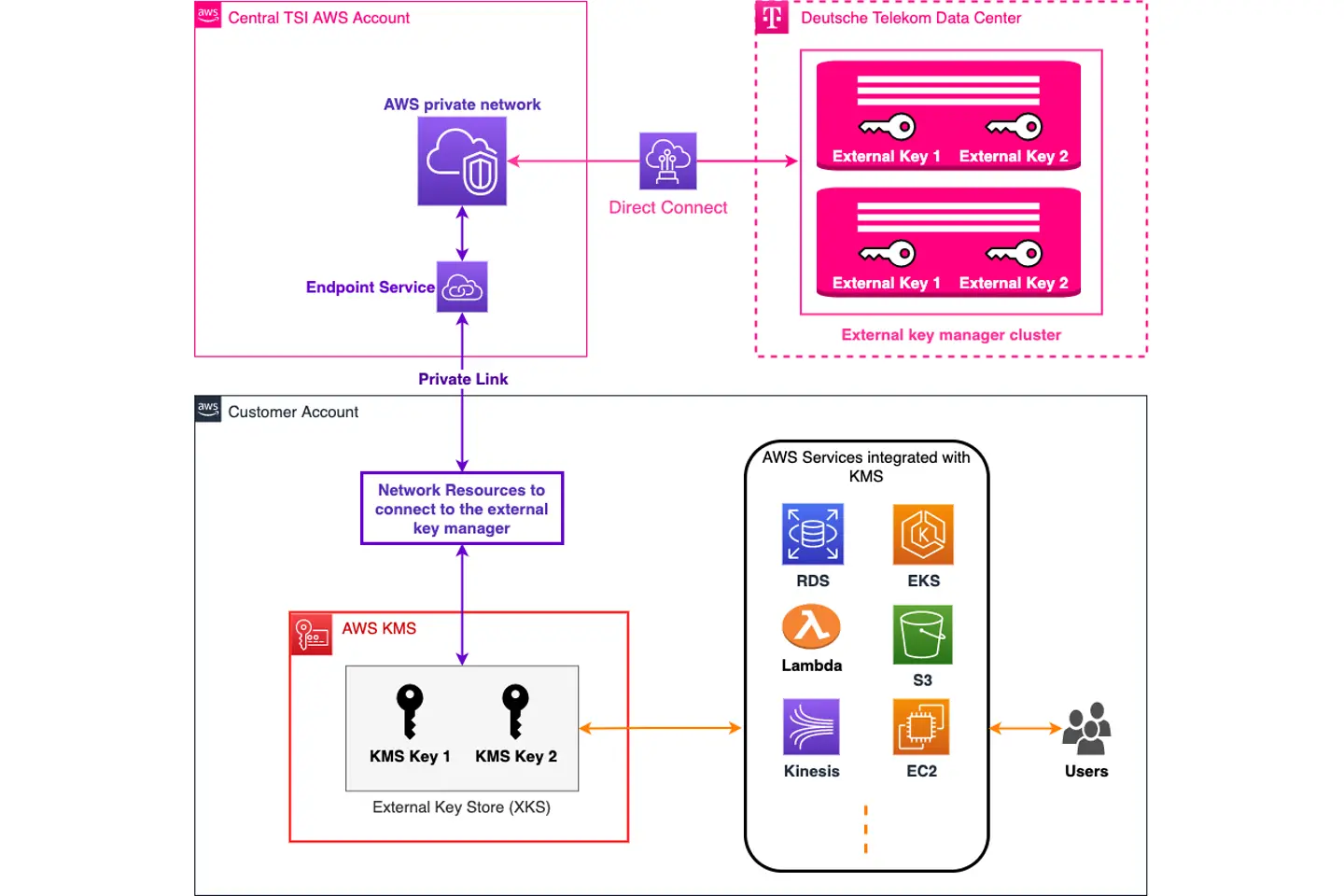
Here is a high level abstraction of EKM:
The external key manager is installed and operated by security experts in Telekom data centers. The multi-node structure in separate geographic locations ensures high availability of the key manager. Backups and key rotations are applied to all keys created in the key manager while adhering to best practices.
Maintaining a secure connection with low latency between AWS XKS and the external key manager in the Telekom data centers was a top design priority. Hence, we use an end-to-end secure IPSec connection over AWS Direct Connect, leveraging our networking experiences and benefitting from our AWS Direct Connect partner status. This connection terminates at a private network we created in a central AWS account owned and operated by T-Systems. We extend the connection from this network to our customers’ AWS accounts using a Private Link service provided by AWS.
When a new customer requests the service, a dedicated domain is created in the external key manager and the Private Link endpoint service is shared with their AWS account. In the customer account, some networking resources must be created to connect the XKS store to the external key manager via the private link. We support our customers to create these resources using an AWS CloudFormation template. After creating the network, T-Systems creates the XKS store for customers and connects it to their domain in the external key manager.
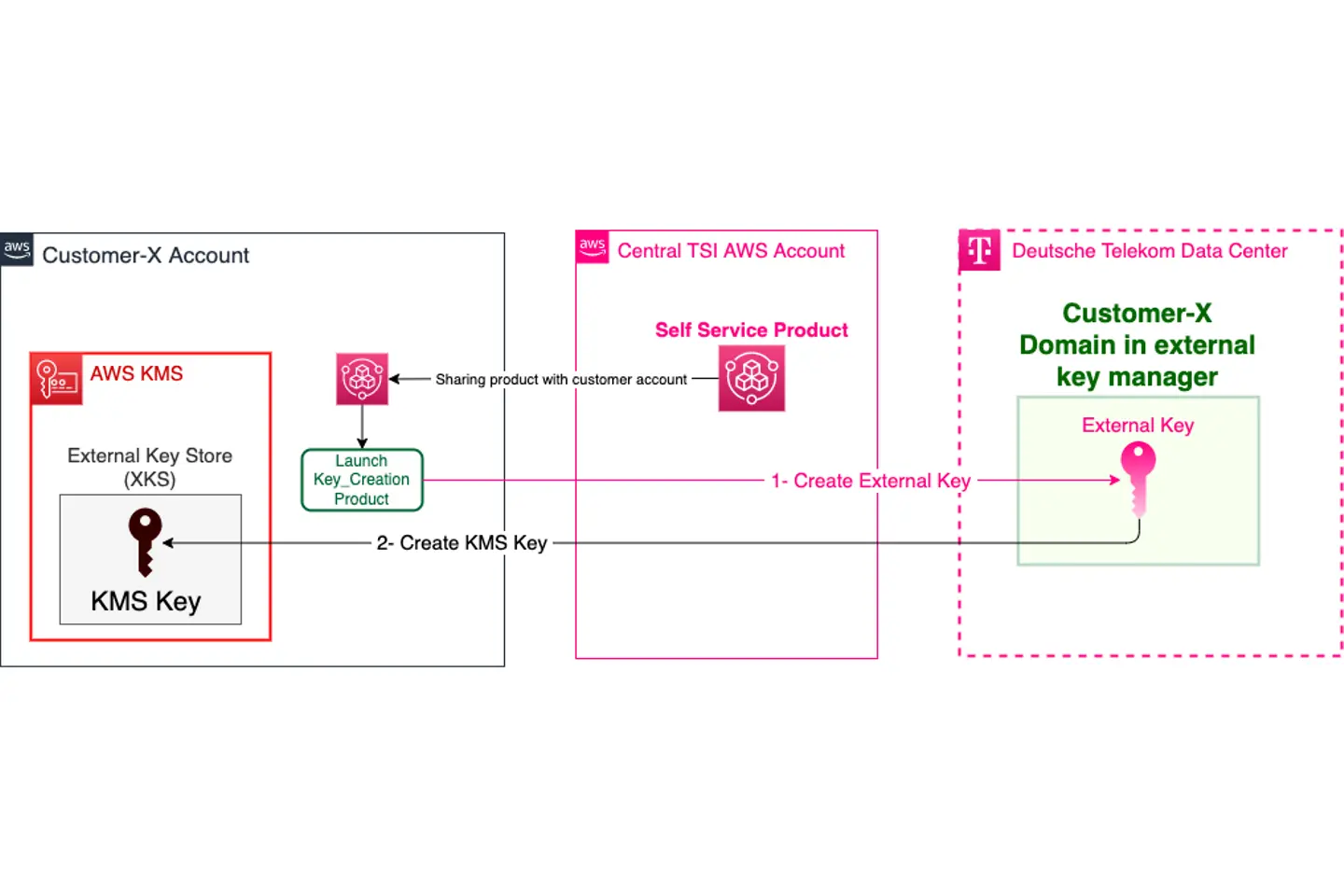
After connecting the XKS store with the corresponding domain in the external key manager, we enable our customers to create XKS KMS keys that are backed by keys created in their domain in the external key manager using our secure and fully automated self-service product. After sharing the product, the customer can specify which IAM roles, users, or groups are allowed to launch and create XKS KMS keys. When an authorized user wishes to create an XKS KMS Key, they can simply launch the product with the following parameters:
The product first creates an external key in the customer domain of the external key manager. Then it creates an XKS KMS key in the named External Key Store that will be backed by the external key.
This post is kickstarting a series of posts about the EKM topic. The follow-up blogs will cover the EKM product in more details explaining in one of them the Network deployment and in the other one the self-service product. We might add another blog also for monitoring and logging.