
The run to the cloud continues. Workloads on AWS – sure! Workloads with sensitive data on AWS? … wait … so far a no-go for most enterprises. Those who want to implement innovations and leverage business potential in new markets need the cloud. But they also must meet regulatory requirements. A European dilemma. How can it be solved?

The healthcare environment in Germany has been pepped up in recent years. Digitalization and its importance for the healthcare sector play a significant role in this. Under the acronym of DiGAs (short for digital health applications), a new market with new business opportunities is emerging.
In addition to established providers of healthcare services, new digital companies with skills in software development also sense their chance to establish themselves permanently on the market–with web services or mobile apps for diagnosis and therapy. First movers have already seized the opportunity and listed their DiGAs at the Federal Institute for Drugs and Medical Devices (BfArM). So far, doctors are able to prescribe a good 30 apps and web services to their patients. And health insurance companies reimburse the costs for it. The new DiGAs support, for example, patients with mental illnesses, metabolic diseases, or cardiovascular diseases.
New apps and web services? Whenever new applications are discussed these days, the cloud seems to appear. It offers a wide range of possibilities for development and operation of these solutions. Cloud-native methods such as containers and DevOps offer a range of options for agile development and innovation. Developers can also use additional services from the cloud ecosystems, for example from AWS, so as not to reinvent the wheel. And if the app takes off, the platform simply scales with the higher demand. Last, but not least, start-ups can easily cope with the financial risk because the pay-as-you-consume principle avoids high investments by only incurring operating costs. There is no need to manage the platform. This allows you to focus fully on the enterprise’s own value add. A dream, …
... which shatters so easily. Personal data requires special protection in Germany; when it comes to social data and health data, the bar is even higher. As reasonable as the use of a US public cloud is from a technical point of view, as a DiGA operated app it is not possible to confront the hurdles for approval in the German health market. In addition to a certificate of conformity for security and functionality, the BfArM also expects a certificate of compliance with the IT baseline protection criteria according to ISO/IEC 27001 since April 2022. Moreover, the goal of the approval hurdle race has not yet been reached: In January 2023, the providers must ensure the data security of their applications is checked by the Federal Office for Information Security to comply with Section 139e of the Social Security Code (SGB) V. This dynamic market with business options is only open to those who meet the regulations. Verifiably.
But what are the specific requirements? Data security covers a multitude of concepts. AWS offers – in addition to a high level of basic protection of the cloud itself – a wealth of services that cover all phases of data security: from preventive protection to the detection of and response to incidents up to the restoration of services. From a purely technical point of view, all tools are there for users to secure their services on AWS. But regulatory requirements go beyond that. Ultimately, all compliance discussions lead to the following questions: Where is my data? Who has access to them? And how can I control that? This not only requires technical solutions, but also the administrative “external environment” must be right. In the case of the personal data processed by DiGAs, this means: They must remain locally and virtually in EEA.
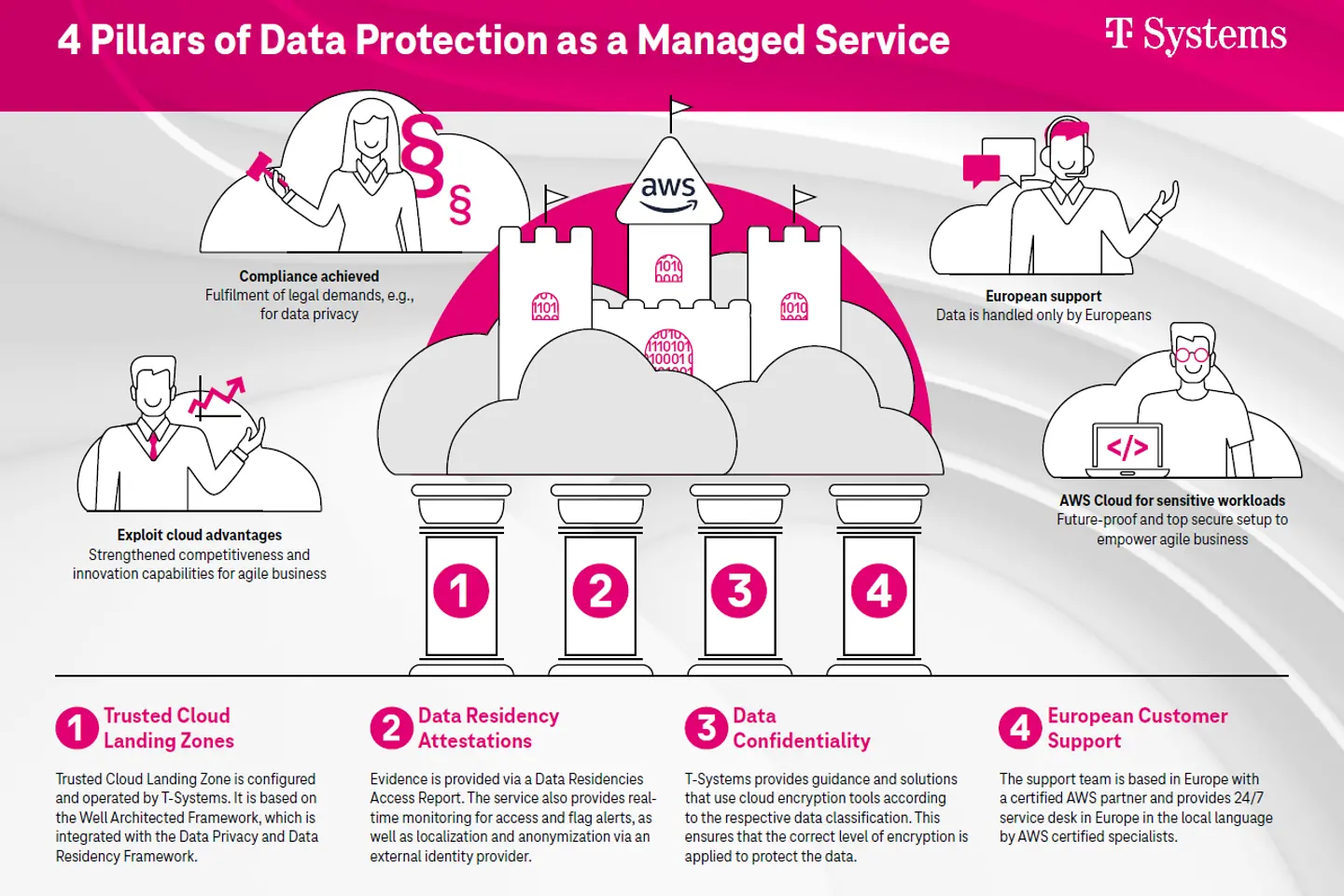
So far, complex projects have been necessary to ensure this. But from the point of view of a provider who carries out projects of this type … many of the tasks needed to meet compliance requirements come up very often. So why not bundle the best practices and turn the countless projects into one product? A product that provides a solid foundation for data confidentiality on AWS and that allows any AWS user to quickly adopt a state-of-the-art security framework. With Data Protection as a Managed Service we have created such a product. It rests on four pillars that meet all relevant security requirements.
This includes:
A nice and complete package with basic security according to current best practice standards, data storage in Europe and management by European staff. Plus, encryption. And yet one question remains unanswered: Where are the keys?
Encryption is an important standard topic for security in the cloud. For convenient encryption usage, cloud providers offer key management systems on their platforms. The integration makes using encryption simple. But the simplicity has a drawback: By storing the cryptographic keys on the platform, the employees of the platform potentially have access to the keys. It's a bit like giving a stranger the PIN of your debit card. To eliminate this risk, it is better to store keys separately, outside the platform. The external key management (EKM) excludes the cloud provider's access to keys.
Such an extra package for security complements the possibilities of AWS and simultaneously opens up the possibility for companies to offer digital innovations even in regulated environments. Workloads with sensitive data on AWS? Previously a "no go" for many companies can become reality with such a package – not only for DiGAs.