
In this blog, find out why software-defined vehicles (SDVs) are gaining steam. What are the customer expectations from these smart automobiles? How’s the market surging for SDVs? Why is it vital to secure the software? Which attacks are on the rise in the market? Find out about the recent attacks on automotive players and what cyber security measures OEMs can take. Also, determine what UNECE R155 regulations are.
Modern customers look at automobiles as a way beyond the means of transport – they have become no less than rolling computers. Users see automobiles as an extended version of their digital lifestyles like smartphones or gadgets. They expect automobiles to be intelligent, be loaded with features that make the driving experience seamless and more importantly personalized. They want smart and connected automobiles – otherwise known as SDVs.
Modern automobiles are more software than metal; they rely heavily on software to manage and control many functions in the automobile. They include advanced infotainment systems, connectivity to external devices, driving assistance, and can receive over-the-air (OTA) software updates (enabled by the cloud) for enhanced functionality.
Automotive manufacturers or OEMs prefer building SDVs, as their functionalities are not set in stone or fixed permanently. With software updates, they can roll out improvements in the functions, offer more personalization, fix bugs, increase car performance, and so on. This constant improvement in features and performance makes an attractive selling point for manufacturers.
SDVs aren’t just about infotainment and personalization. They also offer advanced driver assistance systems (ADAS) – a prominent safety feature used by drivers for driving assistance like cruise control, lane departure warning, collision avoidance, etc.
Sustainability is at the top of the heap today in the market with a lot of buzz around it. SDVs promise sustainability. By addressing performance issues, and improving energy management and fuel efficiency over time, SDVs offer long-term value and extend the lifespan of the automobile.
With such a range of benefits and features, the consumer appetite is growing. There’s been a rise in demand for connected, autonomous, shared, and electronic (CASE) vehicles. This demand is also driven by various government initiatives and policies introduced to promote smart automobile adoption and manufacturing. For instance, from 2035 onwards, the European Union (EU) members will need all new cars to have zero emissions.1
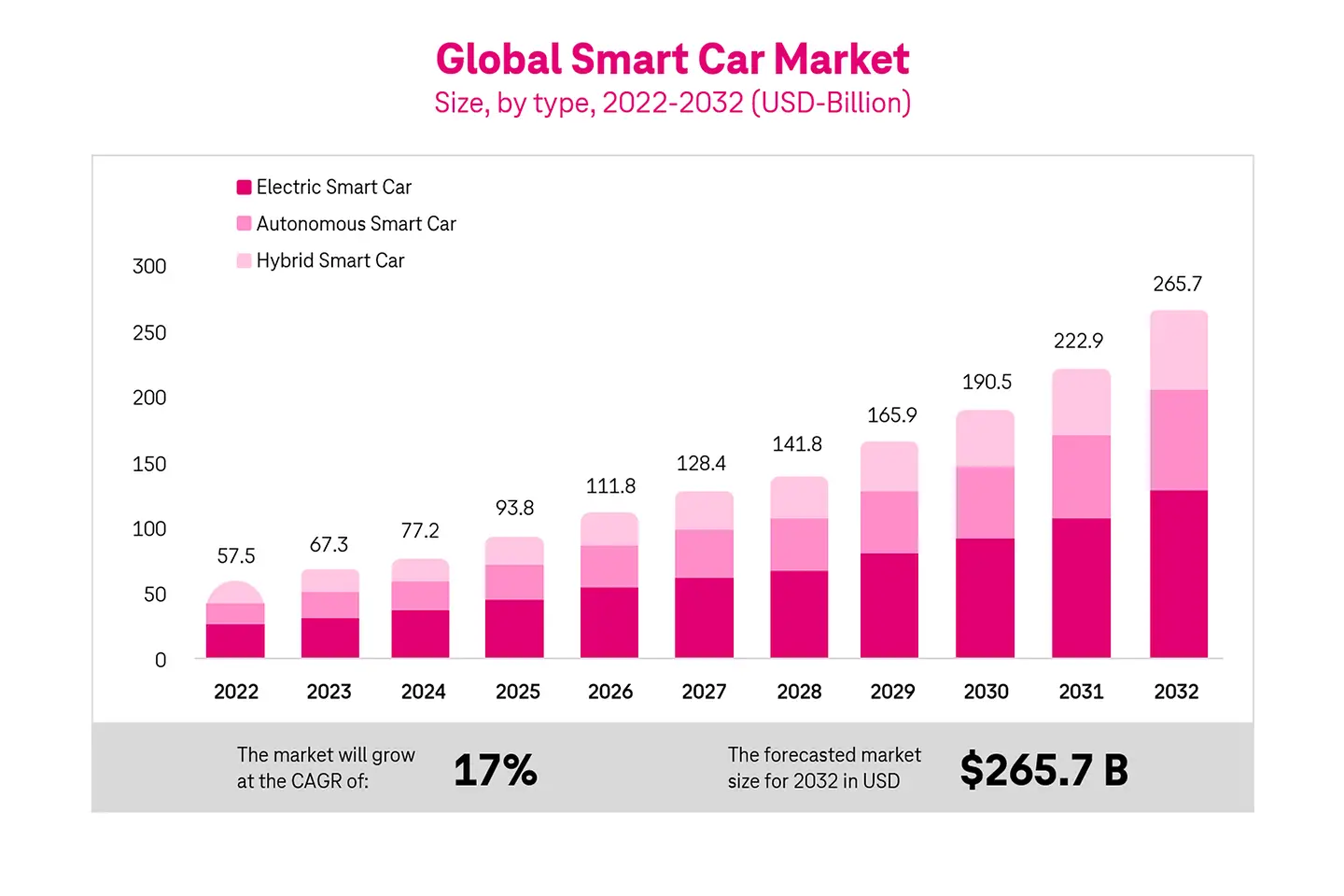
The global market for smart vehicles is set to grow by 17% CAGR. The forecasted market size for 2032 is US $265.7 Billion. This includes smart automobiles like electric, autonomous, hybrid2, etc.
A report by the Boston Consulting Group stated that by 2030, software-defined vehicles will create a value of more than $650 Billion for the automotive ecosystem. The automotive software and supplier market is also poised to double from $236 Billion to $411 Billion during this time frame.3 According to a McKinsey report, about 95% of new automobiles sold in 2030 will be connected and about two-thirds of customers will switch automobiles for a better autonomous driving car.4
These statistics indicate that the collaborations and partnerships between automotive manufacturers and technology or software providers will grow. This fosters rapid scaling, innovation, and a competitive edge. The IT investments are already rising. For instance, General Motors (GM) announced the Ultifi software platform in 2020 for an enhanced vehicle experience. GM anticipates generating revenues of up to $25 Billion annually by providing software-as-a-service (SaaS) products in the vehicles through Ultifi software.5
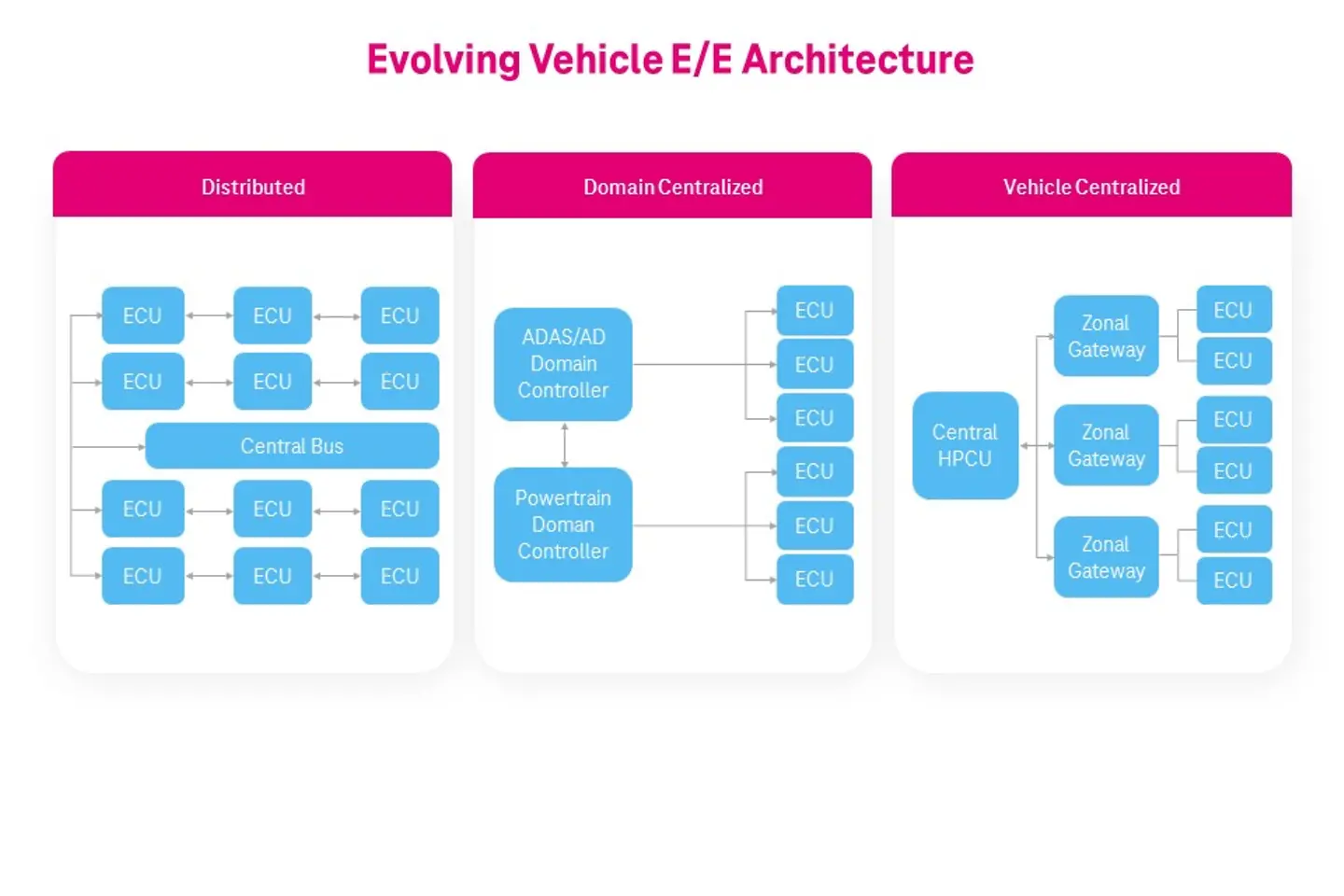
Well, even though the benefits of putting software at the heart of automotive is one thing, it must be protected. Any device with software and connection to the internet is susceptible to hacking, posing potential digital risks. SDVs have complex software algorithms and sensors to navigate the environment. As more digital technologies come into the picture, the attack surface grows along with it – meaning the risks of facing a cyber-attack grow.
SDVs can have as many as 100-150 electronic controller units (ECUs) that are responsible for temperature, fuel injection, braking, and object detection. These ECUs are interconnected and are constantly interacting and exchanging data. Each of these can serve as an entry point for an attacker.
As the architecture gets sophisticated with time, Centralized High-Performance Computing (HPC) platforms are being adapted to reduce the number of individual ECUs and facilitate a standardized development environment. This architecture reduces the number of entry points for hackers. For instance, any automobile that has a remote access feature has a possibility of being hacked. A hacker who has gained unauthorized access to your vehicle may attempt to take control of the critical functions.
In 2022, a white hat hacker claimed that he found a way to hack Tesla electric vehicles by gaining remote access by exploiting third-party software. The hacker could gain access to some functions of the car. But it was just a white hat hacker trying to be curious, an organized group of criminals with sophisticated tools can cause a lot more damage.6
In 2023, some Ph.D. students from Germany tried to gain access to the rear heated seats (hardware) of a Tesla car. By jailbreaking, these students were also able to get hold of user data and some of its internal systems. Tesla’s rear seat heating is a feature that can be unlocked by paying a fee of $300. They managed to activate seat-heating without paying any fee.
More OEMs are rolling out such features - putting hardware and software behind the paywall. For instance, Mercedes-Benz announced that electric EQE and EQS can increase acceleration by paying $60/month. BMW also offers similar paywalled services.7 Users trying to bypass subscriptions by jailbreaking or using rogue software could lead to the launch of malware in the SDVs – which further increases the cyber risks. Over-the-air updates also provide an opportunity for hackers to gain access to vehicle systems. This could involve launching malware that manipulates the data. Imagine, a car not being able to identify maintenance and repair due to data manipulation done by malware. There are several other possibilities. Well, the motive for cybercriminals could also be data theft since these smart automobiles store a lot of users’ personal information.
Some of the common attacks on SDVs are:
There are other attacks like Application Programming Interface (API) based attacks, backend attacks, server attacks, Denial-of-Service (DoS) attacks, and so on. The motivation behind these attacks could be anything from automobile theft, data theft, ransom demand, and more.
In 2023, of all cyber incidents – 37% of them were attributed to data breaches.8
Data breaches could lead to theft of sensitive customer data, personally identifiable information (PII), billing information, location, etc. Such data ends up on the dark web auctioned by criminals for further exploitation. Breaches could also lead to Intellectual Property theft. For example, source code could be stolen to create counterfeit products in the market. All these factors boil down to loss of customer trust, legal actions, fines, decrease in revenues and brand reputations, and so on. In December 2023, Akira ransomware claimed to have launched an attack on Japanese automaker - Nissan (Australia division). Akira warned to expose 100 GB of data related to projects, agreements, and customers if the ransom wasn’t paid.9 This attack came just weeks after another OEM, Toyota, faced a Medusa ransomware attack affecting its European and African services and forcing the company to go offline. Medusa is a double-extortion ransomware – meaning it exfiltrates the data and then encrypts it. In Toyota’s case, customer data and financial data were exfiltrated.1
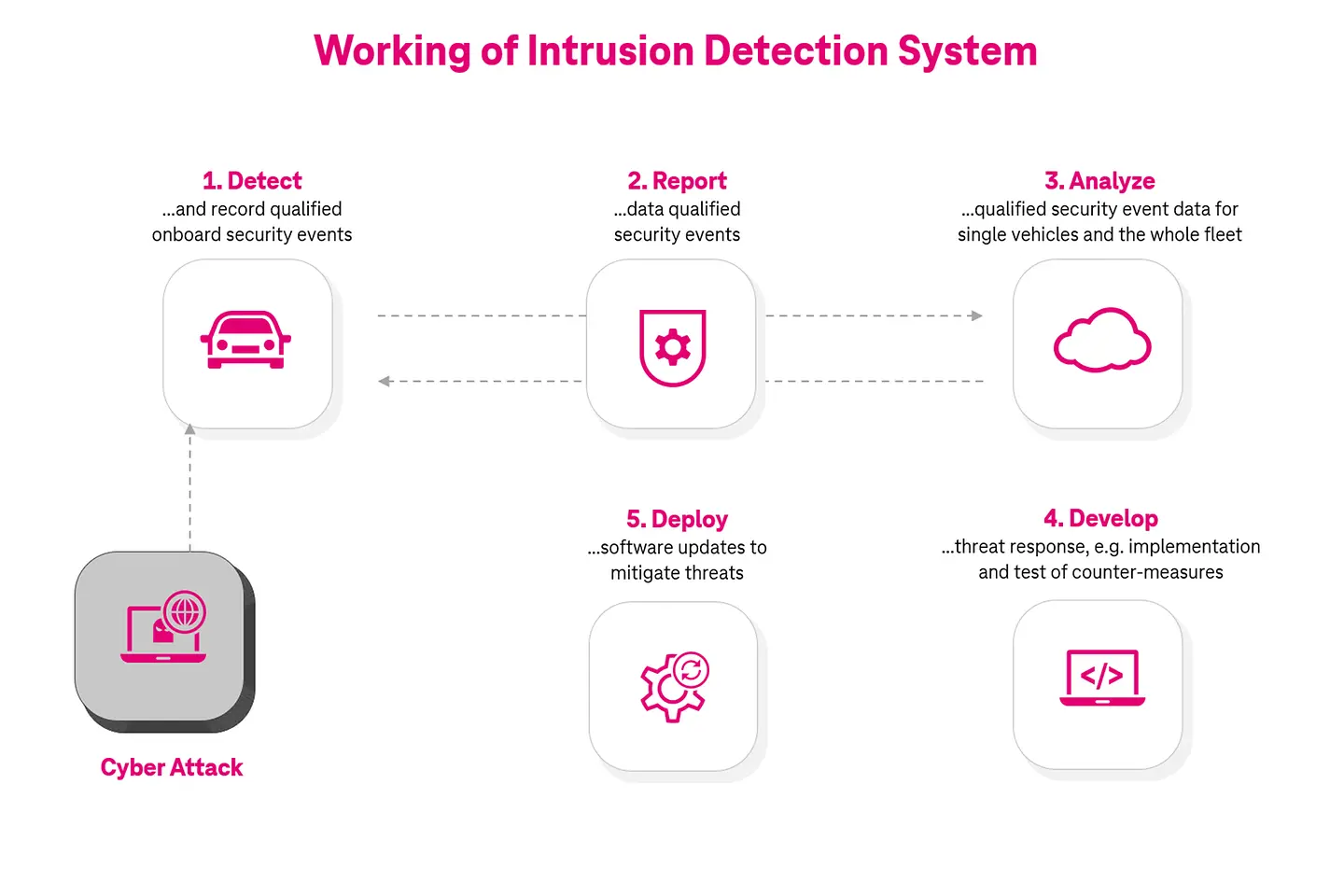
How does an IDS work?
Software-defined vehicles don’t mean it’s an open invitation for the hacker to exploit. With stronger protection measures, they can be protected against digital threats. In-car security can be implemented to protect Electronic Control Units (ECU) and critical systems. This is done by using encryption and authentication methods. Since SDVs rely on networks for continuous communication and updates, network security becomes crucial too. OEMs can use a firewall and intrusion prevention systems to filter and monitor the traffic. Additionally, it imposes stronger encryption and authentication mechanisms ensuring only authorized communication occurs. Let’s talk specifically about intrusion detection systems (IDS).
Given the nature of the attacks and the evolving threat landscape, cars need to have threat detection in real time. IDS fits the bill here. The intrusion detection system monitors network traffic and analyzes patterns continuously. IDS uses signature-based detection to find attack patterns and anomaly-based detection to spot unusual activities. It inspects incoming and outgoing data packets – hunting for suspicious activities. IDS triggers alerts and notifies the security teams or Security Operations Center (SOC) team to respond to the identified threats.
IDS prevents unauthorized access, data breaches, malware infections, and cyber risks. Automakers can use IDS not only for early threat detection and incident handling, but also for better compliance rates.
Penetration Testing is an important approach to assess the security posture of the SDVs. Simulating real-world attacks helps the teams uncover weaknesses and gaps in the architecture, firmware, software, network protocols, and more. Different methods like vulnerability scanning, reverse engineering, fuzz testing, network penetration testing, etc. are deployed to gauge the effectiveness of the existing protection measures. This approach enables OEMs to mitigate risks proactively and fix them before SDVs are launched in the market. With penetration testing, manufacturers can also achieve compliance levels as required by different automotive standards.
Zero Trust enforces strict access controls that continuously verify the identity of any device trying to gain access to a vehicle system or application. As the name suggests, it trusts no user or device, unless the identity and context are verified first. Only authorized devices are granted access to data or applications that they should have access to, and nothing more. It uses the least privilege principle, granting the minimum level of necessary access. By using such strong identity management and encryption protocols, OEMs can secure vehicle data. Apart from identity verification through access control and multifactor authentication, Zero Trust uses the microsegmentation principle.
With microsegmentation, a vehicle’s internal network is divided into isolated zones or smaller segments, thus limiting the lateral movement of attackers in case of an incident. Security controls and policies can be applied to each of these segments differently, depending on criticality. These virtual boundaries can prevent the attack from spreading and causing major damage. Zero trust also secures the application programming interface (API) through communication protocols for in-vehicle systems and external interfaces like mobile apps or cloud services to protect against API-related attacks and data breaches.
Automotive companies also need a centralized management hub to oversee the security policies and responses – hence the need for VSOC. A VSOC sets and enforces policies, ensuring consistent application across the vehicle fleet. The primary responsibility of VSOC is to continuously monitor and respond to threats in real time. Automotive security monitoring involves continuously surveilling network activities, log files, sensors, GPS, cameras, telematics, and system behaviors. Apart from monitoring, VSOC also deploys tools that collect and analyze logs, network traffic, and system activities in real time. This includes detecting patterns, anomalies, potential threats, etc. Any deviations or suspicious patterns trigger alerts, enabling rapid response from the experts to potential threats. VSOC helps vehicle owners, fleet managers, and law enforcement agencies in security monitoring, incident response, asset protection, and data insights.
In summary, these protection measures employ advanced technologies like signature-based detection, encryption, authentication, firewalls, network segmentation, and continuous monitoring. This creates a multi-layered defense system for software-defined vehicles. This technical approach helps identify, prevent, and mitigate threats, safeguarding the integrity and functionality of connected cars.
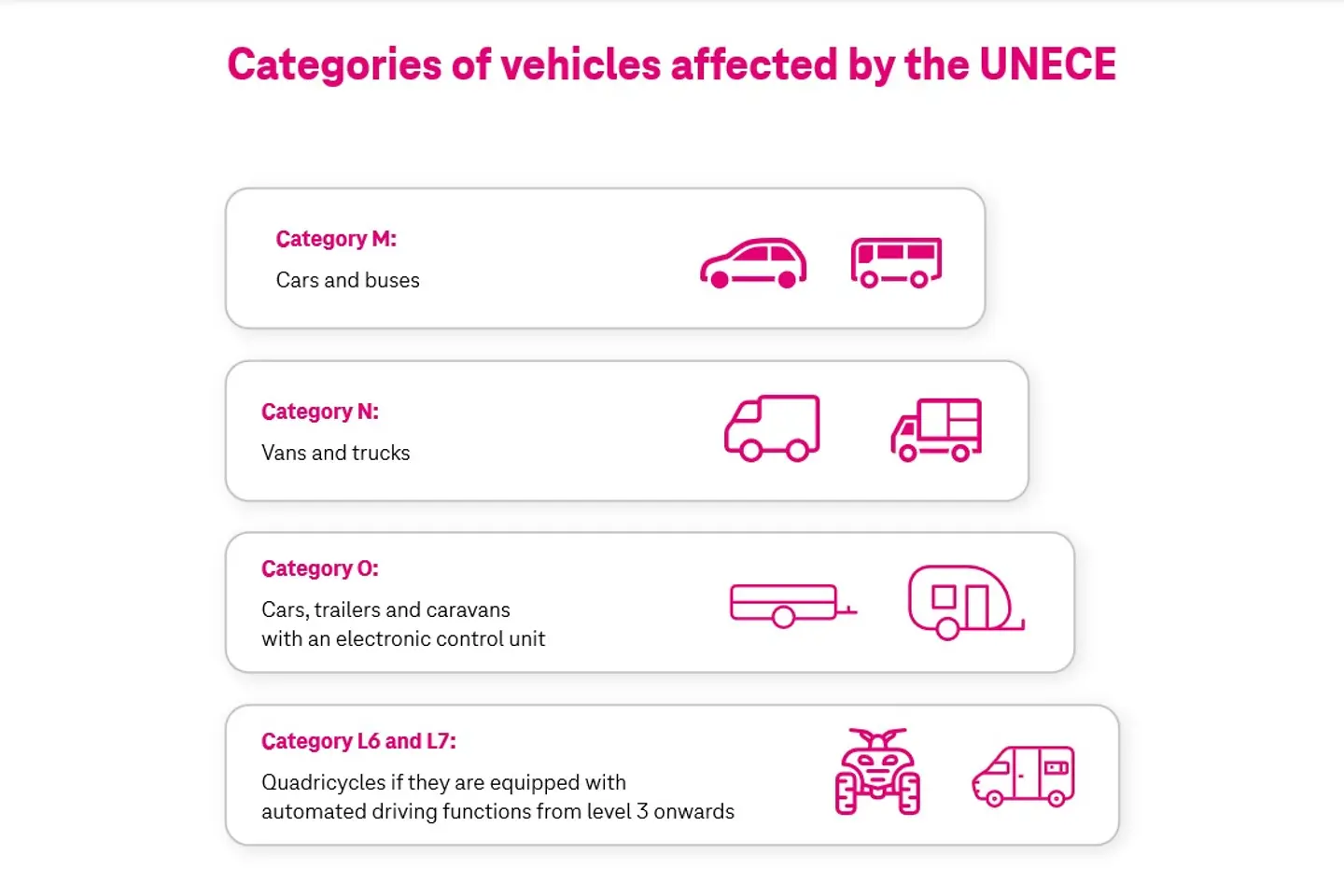
In 2021, the United Nations Economic Commission of Europe (UNECE) enacted first-of-its-kind security regulations UNECE R155, specific to vehicles. The UNECE R155 applies to the automotive industry dealing with connected and automated vehicles (new vehicles produced from July 2024) in the European Union. It has framed guidelines to address potential risks associated with increased connectivity and electronic control systems.
The key aspects of this framework require the manufacturers to:
This regulation applies not only to OEMs, but also to their suppliers because the supply chain risks also have significantly gone up. In addition to R155, R156 has also been enacted concerning software management, software versions, software configuration, documentation, over-the-air update management, etc.
UNECE R155 also directs manufacturers to comply with ISO/SAE 21434 standards, which are broader. R155 emphasizes achieving compliance by defining processes and highlighting the need for security management systems.11 Non-compliance with these regulations may lead to significant fines, penalties, or even suspension of automobile sales in some countries. By adhering to these compliance requirements, an OEM demonstrates a commitment to security, mitigates risks, and avoids heavy penalties. But more than that, they can create a brand reputation, and competitive advantage, and win customer trust.
T-Systems can help you implement robust cyber defense for your vehicles and fleet. With our expertise in automotive and security, we can assist you in meeting UNECE and ISO standards for software-defined vehicles. T-Systems can empower you to integrate strong cyber defense measures like IDS, Automotive Penetration Testing, Zero Trust, Microsegmentation, VSOC, and more. We’re ASPICE (Automotive SPICE) Level 2 certified. Our quality project management and engineering processes are tailored to match your automotive software development needs. With our automotive solutions, create a competitive advantage, manage risk better, improve compliance, and offer quality assurance for your customers. Get in touch with us today.
1 Zero Emission News, 2023, European Commission
2 Global Smart Car Market Report, 2023, Market.US
3 Rewriting Rules of Software-Defined Vehicles, 2023, BCG
4 Rewiring Car Electronics and Software Architecture, 2021, McKinsey & Company
5 GM Blog, 2022, GM Authority
6 Tesla EV News, 2022, Fortune
7 Car Hackers Article, 2023, The Atlantic
8 Global Automotive Cybersecurity Report, 2024, Upstream
9 Akira Ransomware Attack News, 2023, SC Media
10 Toyota Ransomware Attack, 2023, Spiceworks
11 UN Vehicle Regulations Press Release, 2021, UNECE