
In this blog, find out how Operational Technology (OT) systems have evolved over the years, and the usage of SCADA, software, and connectivity has grown exponentially. Can the industry afford the downtime caused by cyber attacks? How does it affect public life? What types of cyber attacks are rising? How can businesses protect against these modern-day cyber risks?
Until a few years ago, the OT world knew only a few cyber security risks. Those were the days of air-gapped architecture and isolated environments – far away from the attacker’s reach. Things have changed drastically now.
More machines are interconnected today. A large volume of sensors, controllers, and actuators are used to manage the operations of these machines. In just the manufacturing industry alone, the number of connected devices will reach about more than 30 billion by 2025.1
The machines communicate and send data through the Internet, corporate networks, and other communication protocols. The use of OT and ICS systems such as SCADA, PLC, and IIoT has also risen.
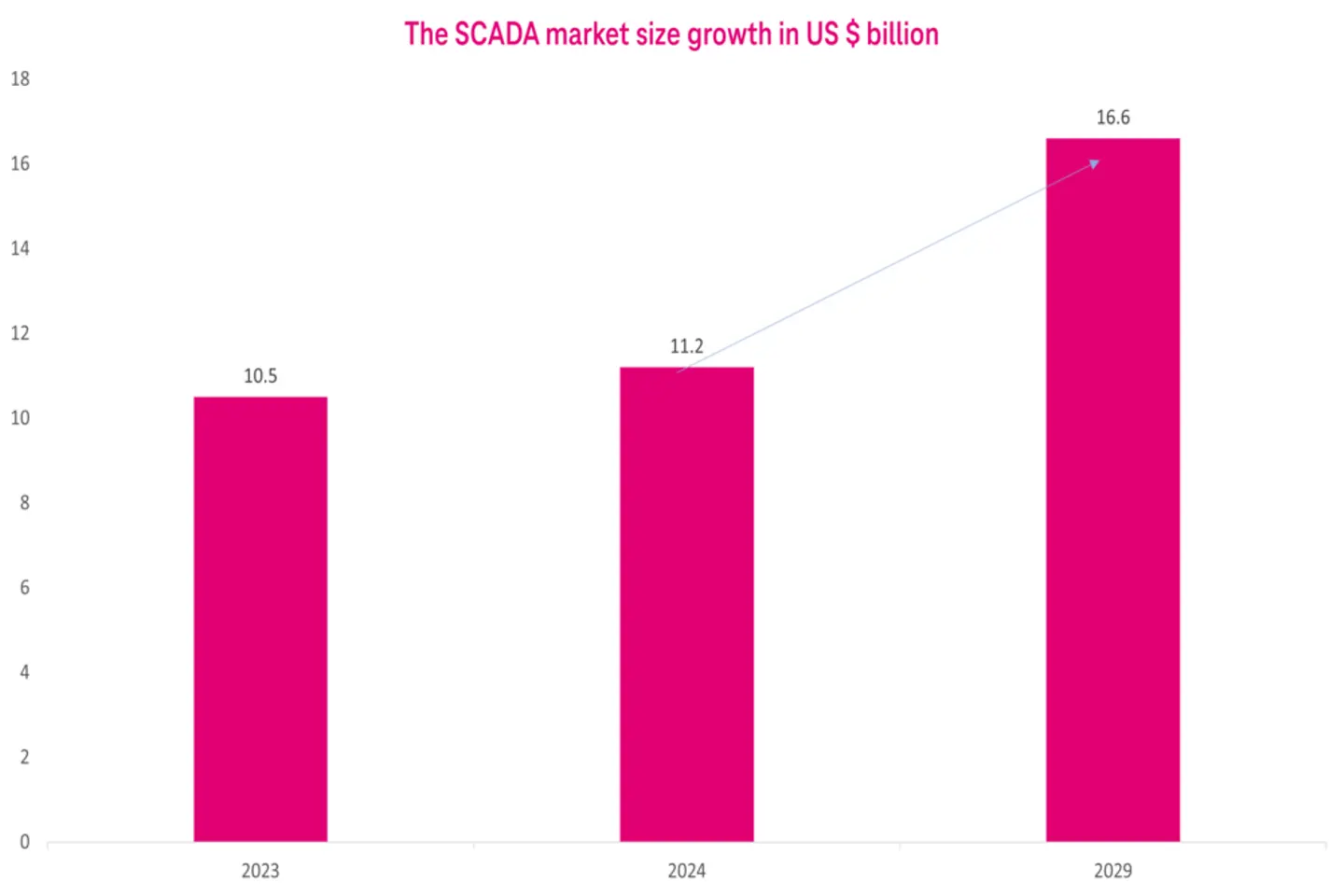
As SCADA adoption rises in the industries globally, its market is also growing at a CAGR of 8.3 %.2 It’s expected to reach USD 16.6 billion by 2029. This growth can be attributed to the Industry 4.0 phenomenon, which is integrating digital technologies with manufacturing and industrial processes. The key emerging technologies are IoT, Artificial Intelligence (AI), Cyber Security, Connectivity, Analytics, Cloud Computing, 5G, and more.
Energy, chemical, water and waste treatment, and oil and gas industries have been using SCADA for quite some time. For instance, water treatment plants use SCADA systems to monitor and control chemical levels, tank levels, environmental conditions, and equipment. It’s also used to check equipment such as filters, pumps, and valves. An operator can adjust the valves remotely based on real-time data, thus maintaining optimum water quality.
However, industries such as transportation and agriculture have also started integrating this new tech to enhance controls, efficiency, and visibility. Transportation companies use SCADA systems to monitor traffic signals, bridges, tunnels, trains, etc. By streamlining and automating the processes, industries save energy. SCADA systems also help in proactive maintenance and avoiding costly downtimes. In agriculture, SCADA is used to get real-time data on crops, soil moisture, temperature, etc.
As the role of software and connectivity in operational technology grows, it leads to an increase in cyber security risks. Industries that use legacy operational technology are more at risk. These systems (designed in the pre-cyber security era) are vulnerable to cyber incidents as they have insufficient in-built security measures compared to the modern threat landscape. Replacing these legacy OT systems is also not too easy. Integrating new systems into legacy, retraining teams as per specialized systems, and reconfiguration of protocols is expensive.
Whether OT systems are new or old, enough security measures need to be in place. Security attacks on OT systems lead to disruption in critical public infrastructure and unavailability of key services.
According to a recent Palo Alto survey, cyber attacks force organizations to shut down 25 % of their industrial operations temporarily. Some interesting data points that have emerged from this report:
Clorox, a US-based manufacturer of cleaning products, faced a cyber attack in 2023 that affected its production capabilities, eventually leading to disruption in its supply chain capabilities.
The manufacturer experienced unauthorized activity and access to its IT systems, which compelled it to take some of the systems offline. The company resorted to manual processes to handle orders and customer communications. Even after a month of this security incident, Clorox struggled to get all operations back to normal levels and restore 100 % of its supply chain. As a result, the product was unavailable in most of the stores temporarily.
This cyber attack cost the company about USD 366 million after posting a 20 % decline in its quarterly net sales.4 The incident emphasizes the fact that attacks not only disrupt operations, but also have far-reaching financial repercussions.
The Clorox incident was an example of an attack on manufacturing. Other notable examples have caused major disruption and impacted public life. The Colonial Pipeline attack is one such case where a ransomware attack caused one of the major US-based pipelines to shut down operations for several days, causing widespread fuel shortages. This led to a week’s downtime, a temporary spike in fuel prices, long queues at the gas stations, and the US President declaring a state of emergency. The corporation was forced to cough up USD 4.4 million as ransom to have operations back on their feet.5
Imagine what would happen if cybercriminals attacked electrical grids. This would lead to a major power outage and downtime in most public services. Modern society cannot function like this. Critical infrastructure must be secured to prevent such chaos.
The motivation behind these cyber attacks could be anything from political to espionage, and plain sabotage to financial. With financial motivations, cyber attackers are launching ransomware attacks frequently on the OT infrastructure. For instance, LockBit is a ransomware type that is known to cause maximum disruption by advanced exfiltration and encryption techniques.
According to Dragos, ransomware attacks have increased by 50 % in 2023 as compared to 2022. 25 % of the ransomware attacks on industrial companies are attributed to LockBit. North America and Europe are affected by ransomware attacks the most.
Besides ransomware, malware, insider attacks, and phishing are also some of the top concerns for organizations. Regardless of the attack type, they have a business impact – financial loss, reputation loss, compliance issues, and so on.
These consequences of attack compel industry players to make the right cyber security investments. Remediation of a single breach for a connected asset costs on an average USD 10,000 to USD 50,000. Considering the financial impact of an attack, it is prudent to invest in security solutions.
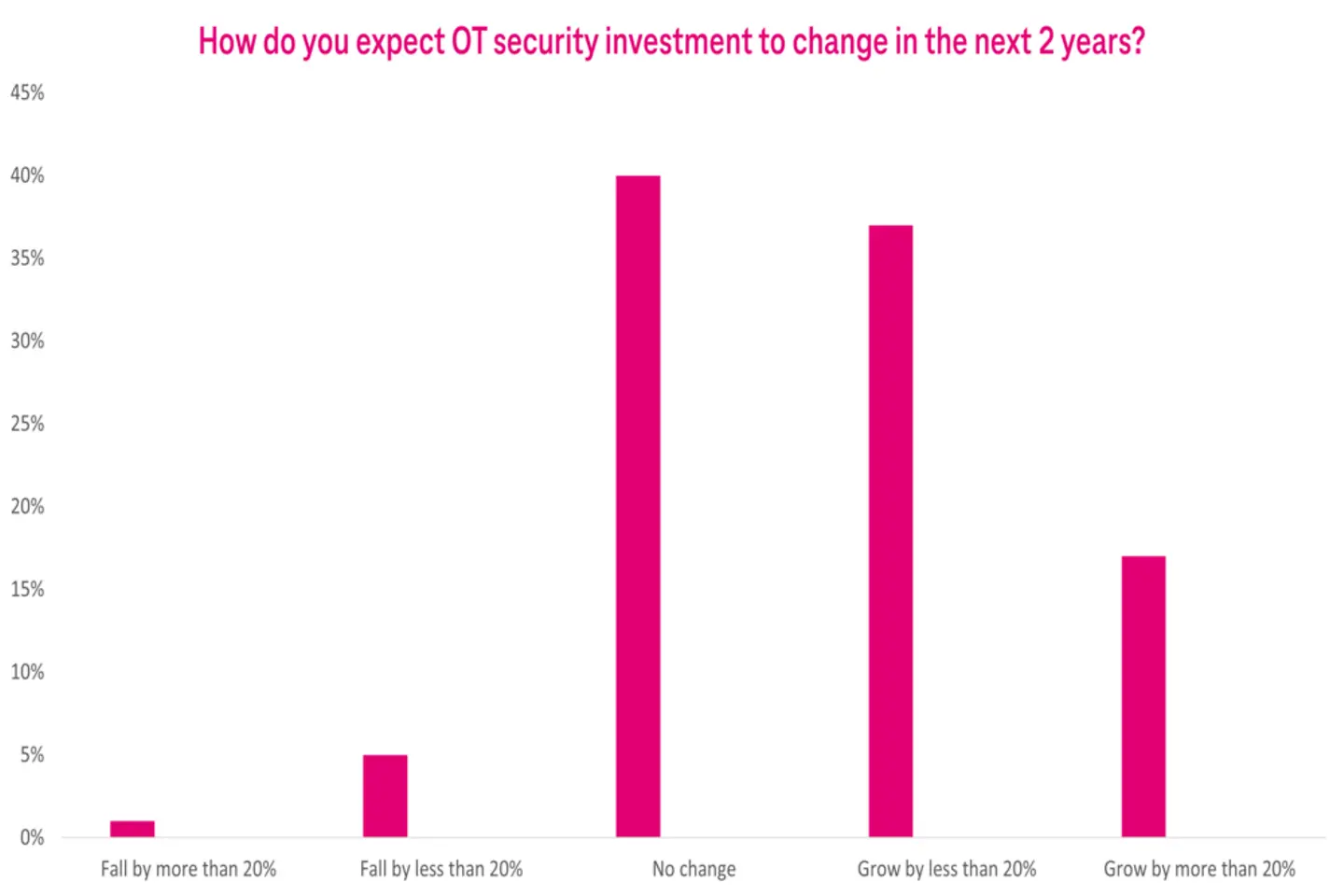
About 97 % of organizations see OT security investment as a priority for the next two years. 25 % of organizations consider it as the top priority. More than 50 % of these organizations are planning to ramp up the security measures by increasing the spending.6
Most of these spends must focus on securing IT since many of the threats originate from IT before disrupting OT. This makes it imperative for OT and IT teams to work together, which is challenging due to departmental silos. However, organizations cannot fully secure their OT and critical infrastructure without tightly integrating OT and IT.
There’s mounting pressure on organizations from regulatory bodies to have OT-IT convergence. 77 % of the organizations expect more pressure from regulations in the next two years. It’s only a matter of time before both departments come together.
Regulatory frameworks such as KRITIS (Critical Infrastructure Act) and NIS2 (Network and Information Security) require operators of critical infrastructure to have a certain level of security measures, incident response, compliance, and risk management. Such frameworks are pushing industries to improve their cyber defense and resilience.
Similar regulations exist all over the world; such as Critical Infrastructure Protection (CIP) Standards by the NERC, National Institute of Standards and Technology (NIST CSF), and so on. NERC has penalized various organizations for failing to adhere to compliance requirements.
One such example is Duke Energy, a leading US-based energy company. This company was fined for over 100 violations of the NERC CIP standards that dealt with inadequate protection of critical cyber assets and failure to implement the required security controls. Duke Energy had to pay USD 10 million in penalties for violations and non-compliance. The company also had to prepare a course of action to implement corrective security measures.7

To that end, what are some of the cyber security measures that companies can implement to protect their critical infrastructure?
In recent years, especially since the COVID-19 pandemic, the remote access trend has taken off. With remote access, operators can control OT systems without being present at the plant or facility. About 3 in 4 OT workers are anticipating that the remote working trend will surge.8 This means organizations will need cloud-based architecture and cloud security measures to manage cloud-borne risks.
The reason for this adoption is quite simple: remote access offers improved monitoring capabilities, real-time response, cost savings, etc. However, it also increases the attack surface and opens the scope for tampering, unauthorized access, ransomware, distributed denial of service (DDoS), malware, and other forms of cyber attacks.
Zero trust security is one of the key security solutions that can help organizations eliminate all kinds of unauthorized access. With zero trust security, user identity and device identity are continuously verified before granting access to OT systems. Users are given access to the data that they need and nothing more than that, which minimizes the attack surface. Organizations can also monitor network activity continuously for any suspicious activity, segmentation breaches, unwanted device communication, data breaches, etc. Moreover, one of the key highlights of zero trust security is network segmentation capability.
With network segmentation, organizations can divide networks into smaller segments and apply granular policies. Segments that have critical infrastructure can have more stringent security policies as compared to others with different resources. Segmentation is effective in preventing the attacker’s lateral movement in the system so that the attack is contained and damage is minimized.
In OT environments, organizations must have TDIR security solutions implemented to identify and stop any threat before it inflicts damage. Networks must be continuously monitored for unusual patterns such as spikes in traffic to any PLC, which could indicate an intrusion.
Once any intrusion is detected, it must be further investigated to understand the cause and extent of the incident. As a part of the response, compromised resources must be isolated to prevent further damage. The recovery and backup process should start once it is ensured that the threat has been eliminated. Reporting the incident to the right stakeholders, including regulatory bodies, is also a part of the response.
For instance, if a water treatment plant detects irregular activity in its pressure levels, then this could mean that the SCADA system could be compromised. The security teams must find the affected systems and isolate them.
Over the last 18 months, around 9 cyber attacks on water plants have been reported in the US alone.9 In some of the attacks, the SCADA systems were remotely accessed by the attackers, and controls were changed. In most of the cases, the attacks were averted before they could inflict greater damage.
In 2021, a Florida-based water treatment plant was hit by an attack where levels of sodium hydroxide were dangerously raised to a level that would have caused poisoning. A report stated that attackers gained unauthorized access remotely to execute this attack. Fortunately, one of the employees noticed an unusual IT system and reported the incident, which led to the discovery of this breach.10
Such incidents place the importance of having the right threat intelligence measures in place.
Security Operations Center (SOC)
SOC can help industries ensure constant vigilance over critical infrastructure. A SOC with expert analysts, and advanced tools, can offer comprehensive vigilance to industries. Analysts can also counter the threats in real time to minimize the impact of the breach. With advanced AI-based tools, threats can be anticipated and mitigated before any OT environments are affected.
Security Information and Event Management (SIEM)
With SIEM, security teams can collect logs from multiple OT and ICS devices for a consolidated view of security events. SIEM can help identify different anomalies. It is also very crucial in the investigation and analysis after a security incident. Additionally, SIEM supports compliance and reporting levels.
Security Orchestration, Automation, and Response (SOAR)
Many industries use SOAR to automate operations and improve response times for quick mitigation and attack containment. When SOC, SIEM, and SOAR are integrated, they can improve security posture – leading to enhanced visibility, efficiency, and response.
Industries with limited security resources professionals, tools, and budgets – can always rely on managed services from industry leaders like T-Systems. MDR security services can help organizations to have 24/7 surveillance of OT networks. With AI-based threat detection tools, both known and unknown threats can be detected and anticipated. Unusual patterns are detected in real time and tackled.
MDR teams can respond and remediate in real time. With the latest tools, they can generate actionable insights and enhance security posture further. MDR also has an endpoint detection and response (EDR) component to secure all devices within the OT environment.
T-Systems offers tailored MDR security to energy, oil and gas, water, utilities, manufacturing, and all other industries that have ICS/OT environments. T-Systems has advanced SOC, modern security tools, and experienced security professionals to help organizations secure their OT-IT infrastructure.
In addition, we can help you identify current security gaps with penetration testing, vulnerability scanning, and other security assessments. Our experts can evaluate your organization’s OT-IT security posture by conducting a thorough asset inventory, finding existing vulnerabilities and unpatched/outdated software, checking access controls, and simulating attacks to find the impact of potential ones.
We have helped businesses with comprehensive security, resilience, and compliance measures as a security partner. To know how your organization can build strong security and resilience, get in touch with us.
1 OT Security Trends, 2024, Verve
2 SCADA Market Statistics, 2023, Markets and Markets
3 OT Security Survey, 2024, Palo Alto Networks
4 Clorox Cyberattack Timeline Article, 2023, The National CIO Review
5 Colonial Pipeline Attack Article, 2022, TechTarget
6,8 OT Security Survey, 2024, Palo Alto Networks
7 Duke Energy Fines Article, 2019, IT Governance USA
9 Cyber Attacks on Water Sector, 2024, Wisdiam
10 Florida Water Utility Hack Article, 2021, Wired