
In this blog, explore why Industry 4.0 presents both opportunities and challenges for manufacturers, with security risks lurking behind its promise. Learn why hackers love targeting these companies, and dive into real-world attacks that cost millions of dollars. Discover how modern security solutions can help safeguard against these threats.
After a brief period of electronic automation, the era of smart automation followed, indicating a close integration of the digital and physical worlds. Industry 4.0, or the Fourth Industrial Revolution was coined about a decade ago in Germany. Digital technologies such as Artificial Intelligence (AI), the Internet of Things (IoT), automation, analytics, and cloud computing flooded the manufacturing floors at the onset of this evolution. The integration became so tight knit that the lines between the physical and digital worlds blurred.
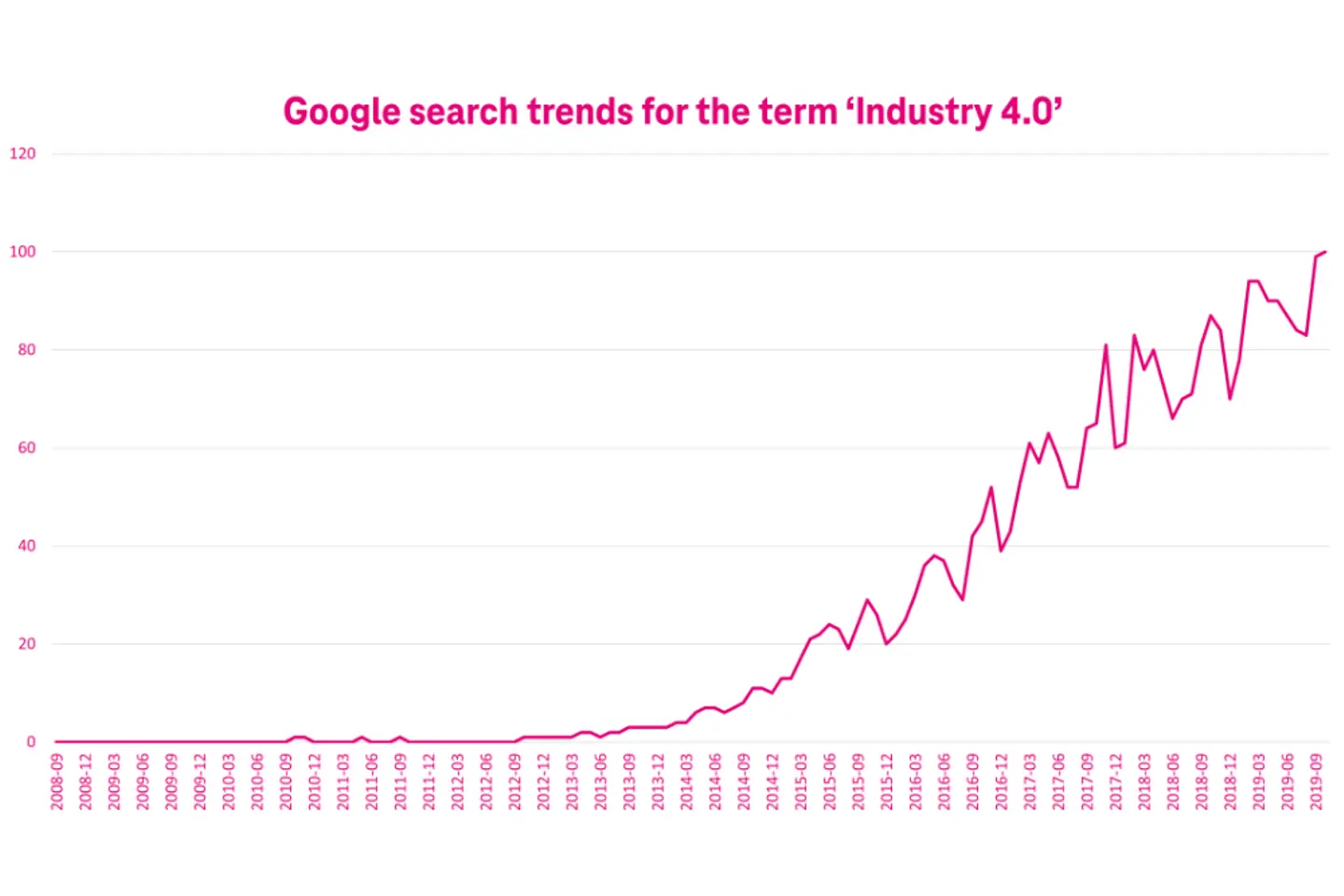
To highlight how the term ‘Industry 4.0’ captured global interest, the adjoining chart illustrates the trend in Google searches over time.
The term invoked curiosity around 2012 and thereafter gained more traction sometime around 2015.1 Ever since then, digitalization in the manufacturing industry has gained steam.
Fast forward to 2024, and the term has evolved from a mere curiosity to something far more substantial, transcending its status as just a buzzword. Manufacturers are increasingly loosening their purse strings to invest more in digital technologies. For instance, the global market size of Industry 4.0 in 2022 was estimated at around USD 130 billion and is set to surpass USD 377 billion by 2029 – growing at a CAGR of 16%.2
With these investments, manufacturers aim to increase operational efficiency and productivity, improve predictive maintenance, enhance quality control, scale better, make decisions based on data, create an efficient supply chain, and so on.
For instance, manufacturers implement cloud technologies to gain real-time visibility into inventory levels. They forecast their demands better and ensure just-in-time inventory levels to minimize excess inventory. German automotive giant Volkswagen uses cloud platforms to improve production performance and supply chain management. Furthermore, the company is rethinking new revenue opportunities by selling its proven cloud-based industry platform to its competitors.3
With digitalization, manufacturers aim to stay competitive and adapt to rapidly changing market conditions. According to a Deloitte study, 86% of manufacturers believe that smart factory initiatives will be the key factors in improving competitiveness.4 Therefore, many manufacturers have increased their technology investments.5
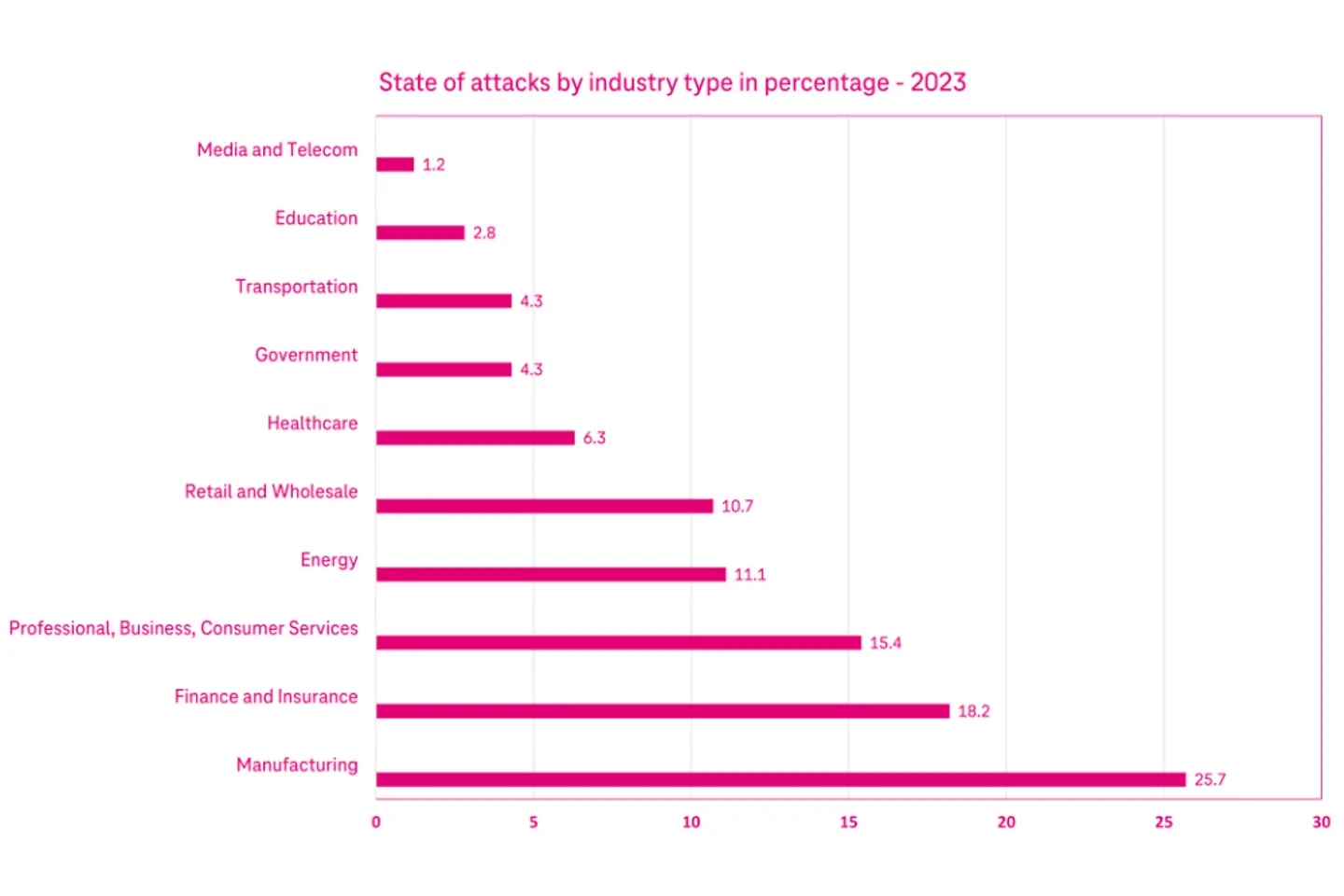
However, introducing digital technologies (Software/IT) in manufacturing creates cyber security risks. According to Statista, the manufacturing sector faced the highest number of cyber attacks in 2023. Almost one in four attacks targeted manufacturing facilities.6 The attacks on this sector are growing year after year.
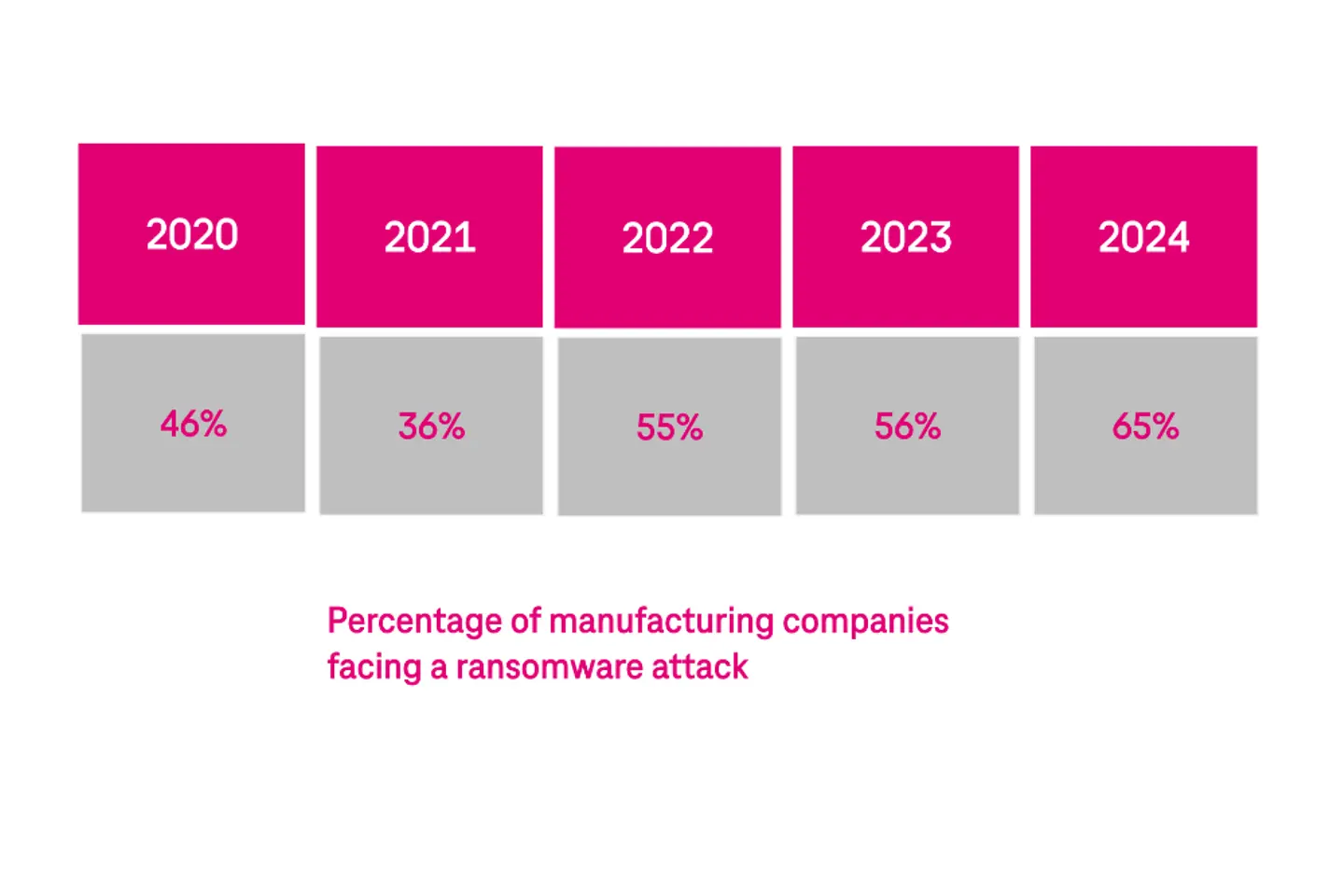
In 2024, ransomware attacks became the most frequent type of cyber attacks, with about 65% of manufacturing companies facing a ransomware attack – up from 46% in 2020.
A typical ransomware attack unfolds when an unaware employee opens a phishing email, clicks on a link, or downloads an attachment. Soon after the employee action, the ransomware spreads within the systems accessing key data and resources. Once it gains access, it starts encrypting and locking down essential files and resources. This brings down manufacturing units, depending on the severity of the attack. Following this, the hackers demand ransom in exchange for the data.
The average median ransom payment stood at USD 1.2 million – most of the manufacturers managed to negotiate the ransom payments. However, it’s worth highlighting that 62% of the companies had to make payments to get the data back.7 This emphasizes the need to have cyber security and recovery solutions in place to minimize the effects of attacks.
Most manufacturing systems are interconnected, especially Operational Technology (OT) and Information Technology (IT) are tightly integrated. With more software, devices, and connectivity, the overall entry points and attack surface increase. Moreover, these companies use legacy systems that are too complex and expensive to replace and upgrade – hence they lack modern security measures. These factors make manufacturing companies lucrative targets for cyber criminals.
Some security incidents can cause major disruption, which leads to production and shipment delays, triggering significant revenue losses. Apart from the financial impact, such disruptions also attract regulatory fines and bad press resulting in loss of customer trust. In more serious cases, equipment failure can pose safety risks for workers. In 2023 alone, more than 500 sites faced physical consequences due to 68 cyber attacks. Attacks targeting critical infrastructure and production units are not uncommon.8
The Colonial Pipeline, a major fuel supplier in the U.S.A., was hit by a ransomware attack that compelled the company to shut down its entire pipeline network to contain the malware. This resulted in fuel shortages, price increases, and panic buying across the eastern United States.
The hacker group DarkSide infiltrated Colonial’s network using ransomware, which encrypted critical data and halted pipeline operations. The attackers gained access via a compromised password linked to an unused VPN account and exploited vulnerabilities in Colonial’s network security practices. Colonial Pipeline shut down its operations to limit the spread of the attack.
This resulted in fuel shortages and price surges across the East Coast. The incident underscored the potential impact of cyberattacks on critical infrastructure and emphasized the need for stronger cyber security defenses across essential service providers.9
Other security incidents have involved hackers damaging Human-Machine Interaction (HMI) components, stopping security systems from being triggered and eventually causing physical damage. There are many notable examples of hackers taking control of critical systems of water utilities or energy companies, leading to facility interference, and eventually disrupting public life due to supply shortages.

In 2023, Clorox, a US-based leading manufacturer of cleaning and household products (with a market capitalization – USD 19.6 billion10), faced a severe cyber attack. The attack led to disruption in its production and supply chain. The manufacturer’s automated systems were also impacted, causing a huge demand-supply gap. The product remained absent from retail stores for weeks. This attack cost the company about USD 49 million – although some reports suggest the losses were close to USD 60 million.11
In May 2024, the company claimed to have restored its inventory levels close to pre-attack times.12 Although the company never disclosed full details of the attack, it is believed that employees fell victim to the hackers' socially engineered tactics. The hackers gained access to several key systems, prompting the company to take systems offline and resort to manual order processing.
Another infamous attack from 2023 was on MKS Instruments, a semiconductor equipment maker, that suffered a ransomware attack. Owing to this attack’s operational disruption, the company missed about USD 200 million in sales targets for that quarter.13 Some reports also suggested Applied Materials (customer of MKS Instruments) – another chip-making company – was impacted by this attack. Their quarterly sales also dipped by USD 250 million due to this supply chain attack.14
Such instances remind us that an attack on one manufacturer can potentially disrupt its customers and partners consequently. About 12-15% of all the attacks are attributed to partner supply chains. The financial repercussions of data breaches resulting from security incidents are also heavy. The global average cost of a data breach stands at USD 4.88 million whereas that of the industrial sector is at USD 5.56 million, which is 13% above the average for all sectors.15 Almost all the companies that face severe breaches opt for cyber security solutions as a knee-jerk reaction. The security approach should be proactive rather than reactive.
Manufacturers must think of segmenting their networks and resources and apply granular security policies for each segment based on criticality. In case of a security incident, the attacker’s movement can be contained to the affected segment only. This limits the damage and company-wide spread of the attack, especially during ransomware attacks where files are encrypted one after another in a short span. Microsegmentation also offers network visibility and control to the security teams.
Billions of IoT devices and other endpoints are deployed today to run smart factories worldwide. Connected devices, including machinery, sensors, and employee endpoints, are prime targets for attackers. Manufacturers need more than just antivirus solutions to defend against advanced cyber risks. An endpoint security solution can identify, block, and respond to threats such as malware, which target vulnerabilities in the endpoint devices.
Modern AI-based endpoint solutions can detect patterns indicative of threats. It can even stop zero-day attacks (new threats), which a traditional endpoint protection solution can miss. AI enables automated responses to threats, minimizing manual efforts. Manufacturing companies can also reduce the number of false positives and relieve the pressure of security teams.
About 32% of industrial organizations already leverage automation and AI. Companies that use full-scale AI along with automation save USD 1.9 million compared to those that don’t use these technologies.16
Manufacturing companies use Industrial Control Systems (ICS), and therefore they require a special security solution to monitor unusual behavior and threats within the industrial environment. At times, IDS is a part of a comprehensive EDR solution that has advanced threat detection capabilities. IDS security is very useful in an industrial setting with legacy systems.
Zero trust security is one of the most effective ways to stop unauthorized access to a company’s resources. Zero trust security enforces strict identity verification and access controls for all users and devices trying to access network resources. With continuous verification of identity, only authorized users are given access. This approach mitigates insider threats and prevents Advanced Persistent Threats (APTs), which otherwise can potentially remain in the network for too long without getting noticed.
With the zero-trust security model, manufacturing enterprises can reduce the attack surface by hiding critical applications from unintended users, minimizing risk exposure, and ensuring strict policy and access controls for OT and IT environments. Remote users can access corporate applications or OT systems through a secure network from anywhere. Traditional perimeter-based security or Virtual Private Network (VPN) solutions are not enough for companies with devices and users outside the corporate network.
Apart from having a good security solution stack, organizations should also invest in regular cyber security audits and assessments to find gaps in the existing architecture. Penetration testing can identify existing vulnerabilities in the system that can be fixed. Outdated systems can be updated through patching. Adopting this proactive security approach is a crucial step for any organization because many attacks arise due to attackers exploiting weaknesses in the systems.
Moreover, inculcating a strong security culture within the organization is essential for safeguarding its systems effectively. Security solutions are important, but they may not be 100% effective, especially where employees easily fall victim to phishing and socially engineered campaigns by hackers. Responsibility must be shared—from the leadership to the rank and file. Companies that invest in building a security culture demonstrate higher resilience to security incidents. They can bring risks from 60% to as low as 10% through awareness programs alone.17
Our Managed Detection and Response (MDR) solution provides comprehensive, 24/7 protection, combining cutting-edge technology with expert services. Our MDR offering includes a fully managed Security Operations Center (SOC) that leverages AI-based threat detection to identify and neutralize threats in real time. Our automated incident response capabilities help contain attacks and minimize impact, while continuous monitoring ensures your IT and OT environments are protected around the clock.
Our security consulting services offer expert guidance on customized security strategies, proactive vulnerability management, and comprehensive compliance support. We also guide companies in achieving compliance with regulations such as NIS2, GDPR, KRITIS, and more. This holistic approach not only defends against advanced threats, but also helps optimize your overall security framework by addressing risks before they become incidents.
By partnering with T-Systems, manufacturers can benefit from stronger security, including reduced downtime, compliance assurance, protection of critical assets, minimized breach impact, and improved productivity. Our MDR solution ensures your business is resilient against today's evolving cyber threats. Get in touch with us today.
1 Google Trends for Industry 4.0 search term, 2024, Google
2 Industry 4.0 Market Size Press Release, 2023, Global Newswire
3 Automotive Industry Article, 2023, CIO Magazine
4 Manufacturing Execution Systems, 2022, Deloitte
5 Tech Trends in Manufacturing, 2024, Gartner
6 Top Industry Cyber Attacks, 2023, Statista
7 State of Ransomware Attacks, 2024, Sophos
8 Threat Report in Manufacturing, 2024, Waterfall Security
9 Colonial Pipeline Attack Article, 2022, TechTarget
10 Market Capitalization Data for Clorox, 2024, Companies Market Cap Website
11 Clorox Cyber Attack Article, 2024, Security Week Magazine
12 Clorox Earnings Post-Attack, 2024, Supply Chain Dive
13 MKS Instruments Ransomware Attack Article, 2023, Bankinfo Security
14 Ransomware Attack on Chip Manufacturer, 2023, ThreatDown
15 Cost of Data Breach Report, 2024, Security Intelligence
16 Cost of Data Breach Report, 2024, Security Intelligence
17 Security Awareness Training Effectiveness Article, 2022, Usecure