
As cyber attacks remain a concern, chief information security officers (CISOs) push for higher budgets and more tools to secure the infrastructure, but this doesn’t always translate into improved security. Is ‘security platformization’ the solution? Find an answer to this and other questions. Explore examples of how companies are improving ROI and simplifying their security operations (SecOps).
The speed and scale of cyber attacks in recent years have been nothing short of alarming. By the end of 2025, the global cost of cyber crime is projected to reach a staggering $10.5 trillion and is expected to rise even further in the coming years.1
The average cost of a data breach stood at $4.88 million in 2024, underscoring the need for businesses to take cyber security measures seriously.2 Fortunately, many organizations are already doing so – CISOs are increasingly pushing to make cyber security a boardroom priority.
C-suite executives are also rethinking their security strategies by increasing their security budgets.3 Gartner estimates that security spending in 2024 reached approximately $183 billion, with projections indicating a 15% growth to $212 billion by the end of 2025.4
This surge in spending comes as organizations adopt more cloud technologies and generative AI (GenAI) – both of which contribute to an expanding attack surface and create lucrative opportunities for attackers.
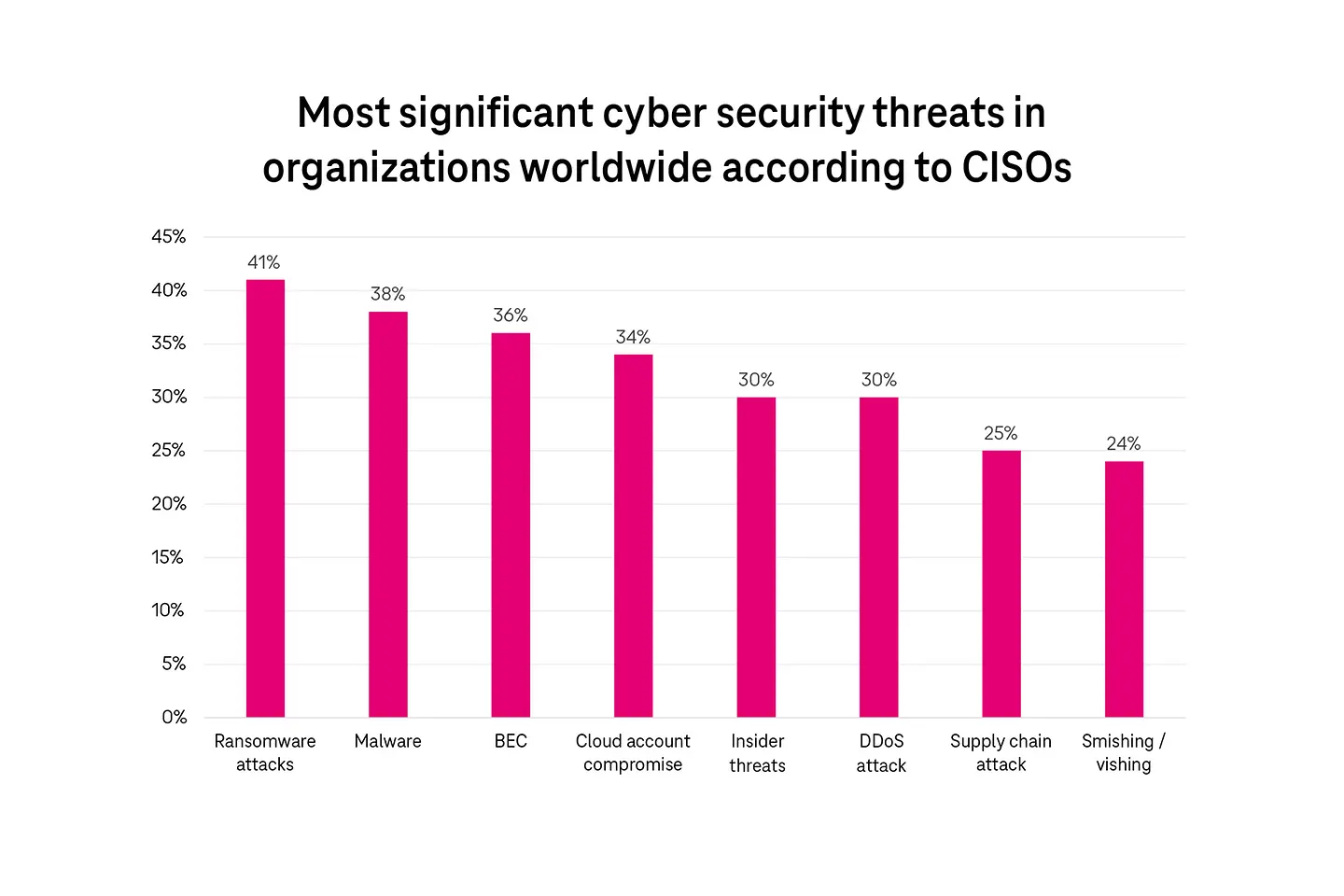
CISOs are particularly concerned about ransomware attacks, followed by malware and business email compromise (BEC). Other prominent threats include cloud account compromise, phishing, insider threats, supply chain attacks, and distributed denial-of-service (DDoS) attacks.5
To tackle these threats, security teams deploy a range of solutions, including endpoint detection and response (EDR), email security gateways, firewalls, cloud access security brokers (CASB), identity and access management (IAM), multi-factor authentication (MFA), data loss prevention (DLP), encryption solutions, and more.
However, in doing so, organizations often end up with too many point security solutions. On an average, organizations juggle more than 80 security tools from 29 vendors.6 Yet, having more tools doesn’t make a CISO’s job any easier – in fact, it does the opposite. Security tools generate an overwhelming number of alerts, keeping security teams and analysts not only busy, but also exhausted.
False positives are a major security challenge today, with 76% of security professionals reporting that low-priority alerts and false alarms slow them down. Imagine teams spending hours investigating an alert, only to discover it's a false alarm.7
This overload can also lead to critical alerts being overlooked simply because teams don’t have the time to verify each one. One of the most infamous attacks on the US-based retail giant Target occurred because its security team failed to act on an alert. They dismissed it as a routine false positive – only to later realize it was a genuine threat. The breach resulted in 40 million customer card details being stolen, costing the retailer over $18 million in legal settlements.8
This case highlights a crucial fact: alerts alone aren’t enough if security teams can’t see the full context. More security tools mean more alerts, but they don’t necessarily lead to better protection – especially when tools don’t communicate with each other or provide the right context. Stitching together siloed data from multiple tools requires a high level of expertise and effort. Meanwhile, cyber security remains an understaffed field, with fatigue being a common issue among security teams. Today, there are over one million unfilled cyber security positions globally.9
When managing a large stack of security tools, organizations face additional challenges such as:
As security complexity grows, ROI takes a hit. Many security tools have overlapping features, increasing overall costs. About 80% of executives have a mandate to cut costs, yet new threats, tool fragmentation, and vendor sprawl make this increasingly difficult. Managing vendor contracts, renewals, and ensuring compliance adds even more administrative burden.
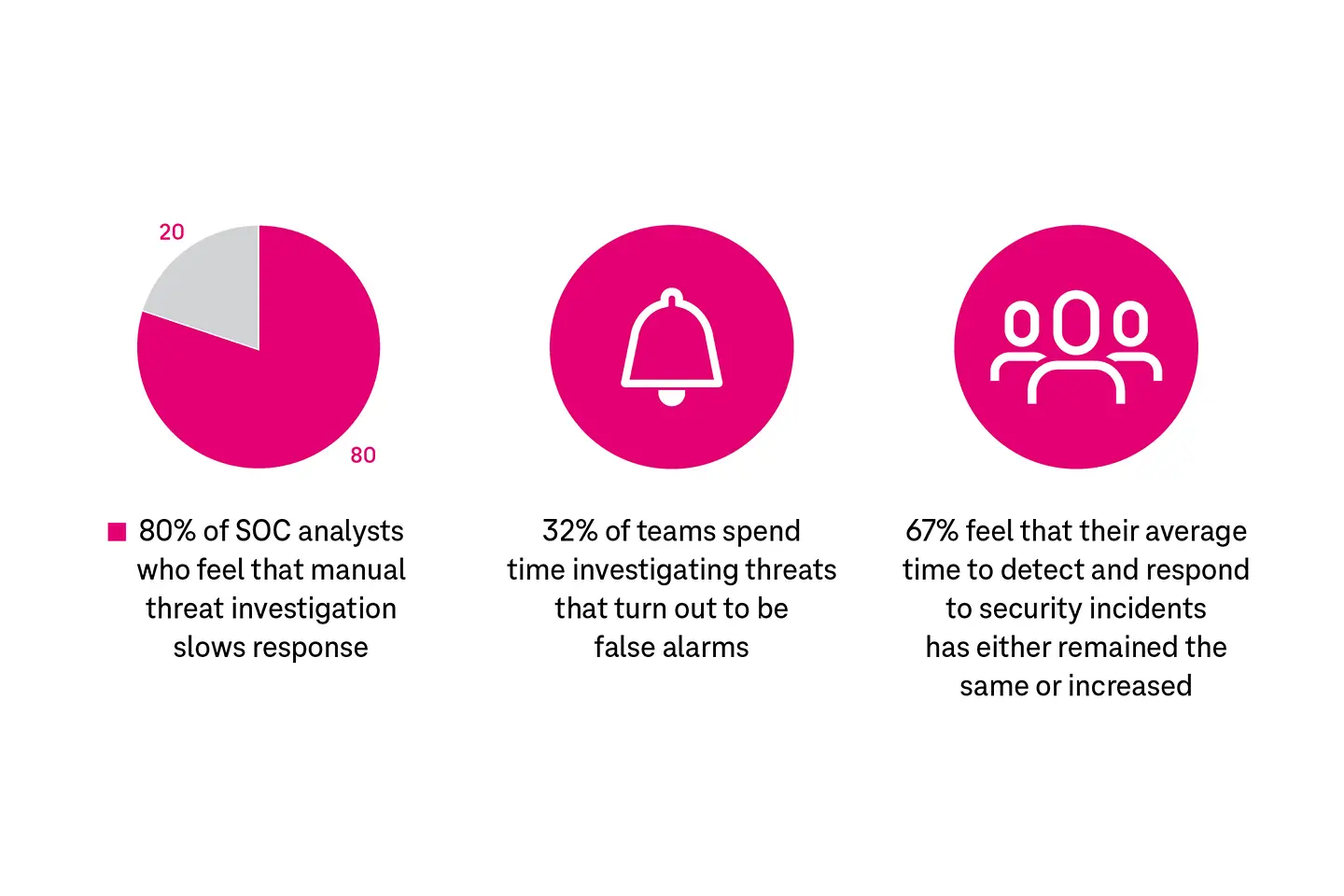
The lack of an integrated tool and excessive fragmentation makes automation challenging, further slowing down threat detection. Some eye-opening statistics:
So what can make security teams' jobs easier? The answer is: reduced number of alerts, grouped alerts, single dashboard, more visibility, automated response, faster detection, and much more. At the end of the day, CISOs want to reduce operational complexity and total cost of ownership (TCO) – and show better security ROIs.

Security teams believe that a consolidated security platform with AI, automation, and real-time notifications can simplify security operations and reduce workload. These benefits may have seemed far-fetched a few years ago, but that’s not the case anymore. Security companies such as Palo Alto Networks are adopting a platform-based approach, unifying capabilities to help businesses consolidate solutions and reduce complexity.
For instance, an organization no longer needs to purchase a firewall from one vendor, a cloud security solution from another, and a separate tool for cloud detection and response. If a single platform can provide these capabilities, security teams can work more efficiently and manage threats more effectively.
However, does this simply mean bundling products and selling them at discounted prices? Platformization (or a platform-based approach) goes beyond that. A unified platform ensures that tools are built to work together seamlessly as one cohesive system.
While bundling may appear to save money on paper, a true unified platform integrates functionalities and shares data, leading to smoother operations and faster threat response. In the truest sense, a platform-based approach is a more pragmatic choice for organizations.
Nikesh Arora, CEO of Palo Alto Networks, has frequently emphasized in interviews and on social media how a unified platform with a single management and policy pane can simplify complexity and configuration challenges for businesses. Palo Alto Networks' security platforms, which feature best-of-breed solutions, enable a faster threat response, ultimately helping businesses reduce TCO and achieve significant cost savings.
The platform approach is relatively new in cyber security, but successful examples already exist in the broader IT industry. Salesforce offers a customer relationship management (CRM) platform along with customer engagement and service modules. Microsoft provides collaboration and productivity applications under a unified ecosystem. Oracle delivers financial management and supply chain tools as part of an integrated suite.
What sets these platforms apart from the competition is their ability to provide an integrated offering that combines multiple business functions, ultimately simplifying operations and improving efficiency.
A unified security platform offers more value for your business. Here are some key benefits:
A survey conducted among organizations that have adopted a security platform revealed the following insights:
As of today, Palo Alto Networks offers three platforms powered by artificial intelligence (AI) and machine learning (ML):
These platforms enable automated detection, prevention, and remediation. Individually, they incorporate the capabilities of various standalone security products but are now tightly integrated to simplify operations and efficiency.
A US-based consumer goods company, Colgate-Palmolive, secured its manufacturing setup using a unified security platform. With this approach, the company enhanced visibility across its network and IT infrastructure. The company improved SOC efficiency. It also boosted performance of over 900 critical applications.
The platform blocks over 200,000 unique threats per month, significantly reducing security risks. Additionally, six different security tools have been integrated into a single platform and console, reducing operational complexity and improving collaboration.12
Integrated security tools:
Several companies are transitioning to a comprehensive security platform to meet their security objectives. For example, the world’s largest bakery, Grupo Bimbo, has implemented Palo Alto Networks' security platform to reduce security risks and simplify operations. They have cut costs by approximately USD 100,000 per month by eliminating the need for multiple point products. They have automated security processes, reducing mean time to resolution (MTTR) from days to just one hour.13

More enterprises are reconsidering their security strategy, especially when it comes to consolidating security products. Platform adopters are projected to achieve:
As a trusted managed security service provider (MSSP), T-Systems helps businesses implement a comprehensive security platform strategy. Our consulting security services and assessments identify risks and vulnerabilities that could impact business continuity and reputation. We enable businesses to successfully adopt security platformization through strategic guidance, seamless integration, and 24/7 monitoring. With eight global SOCs, 2,400 security professionals, and a global footprint, we have it what it takes to integrate PANW security platforms smoothly, ensuring you achieve the most gains.
With T-Systems’ security services, businesses:
Our advanced security solutions provide scalability and future-proofing against evolving threats. Managed Detection and Response (MDR) offers real-time threat detection and rapid response. SASE integrates cloud security and network protection. Microsegmentation restricts lateral movement to prevent internal threats. Automated penetration testing proactively identifies and mitigates vulnerabilities.
Stay ahead of cyber threats – leverage AI-powered security platforms and the expertise of T-Systems and Palo Alto Networks.
1 Cyber Crime Statistics, 2025, Astra Security
2 Data Breach Report. 2024, IBM
3 Global Digital Trust Insights Survey, 2024, PWC
4 Security Spending Forecast, 2024, Gartner
5 Cyber Security Threats, 2024, Statista
6 Capturing the Cybersecurity Dividend, 2025, IBM
7 Global SOC Study Results, 2023, IBM & Morning Consult
8 Target Data Breach, 2023, Card Connect
9 Cybersecurity Jobs Report, 2025, Cybercrime Magazine
10 Global SOC Study Results, 2023, IBM & Morning Consult
11 Capturing the Cybersecurity Dividend, 2025, IBM
12 Colgate Palmolive Customer Article, 2024, Palo Alto Networks
13 Grupo Bimbo Customer Article, 2024, Palo Alto Networks
14 Business Value of PANW Platforms, 2024, IDC