
In this blog, find out how security operations (SecOps) have evolved from reactive to proactive. Find out the pitfalls of manual operations and the burnout security professionals experience. How can these challenges be eliminated by Artificial Intelligence (AI)? Are companies adopting Artificial Intelligence? What benefits can Artificial Intelligence promise and deliver in SecOps?
For a long period, the Security Operations Center (SOC) meant a huge room with big screens constantly flashing alerts. To these screens, hooked were security teams – continuously monitoring and analyzing alerts. The SOCs were originally established for government and defense organizations focusing mainly on network alerts. Then came intrusion detection systems (IDS), firewalls, anti-virus, etc. SecOps got sophisticated to keep up with the growing threats. For instance, security information and event management (SIEM) were added sometime in 2005 to detect threats and respond to them better (incident detection and response).
As cyber risks kept evolving, especially advanced persistent threats (APTs), the tools to fight these risks were also sharpened. From 2016 onwards, the market started witnessing the phenomena of Managed Detection and Response (MDR) services with modern threat-hunting capabilities. Security operations (SecOps) have gone from being reactive to proactive. Enter 2024, technologies like automation and artificial intelligence are getting fully integrated into security operations. Technologies like Artificial Intelligence help businesses cut through the noise, process data better, and resolve threats efficiently.
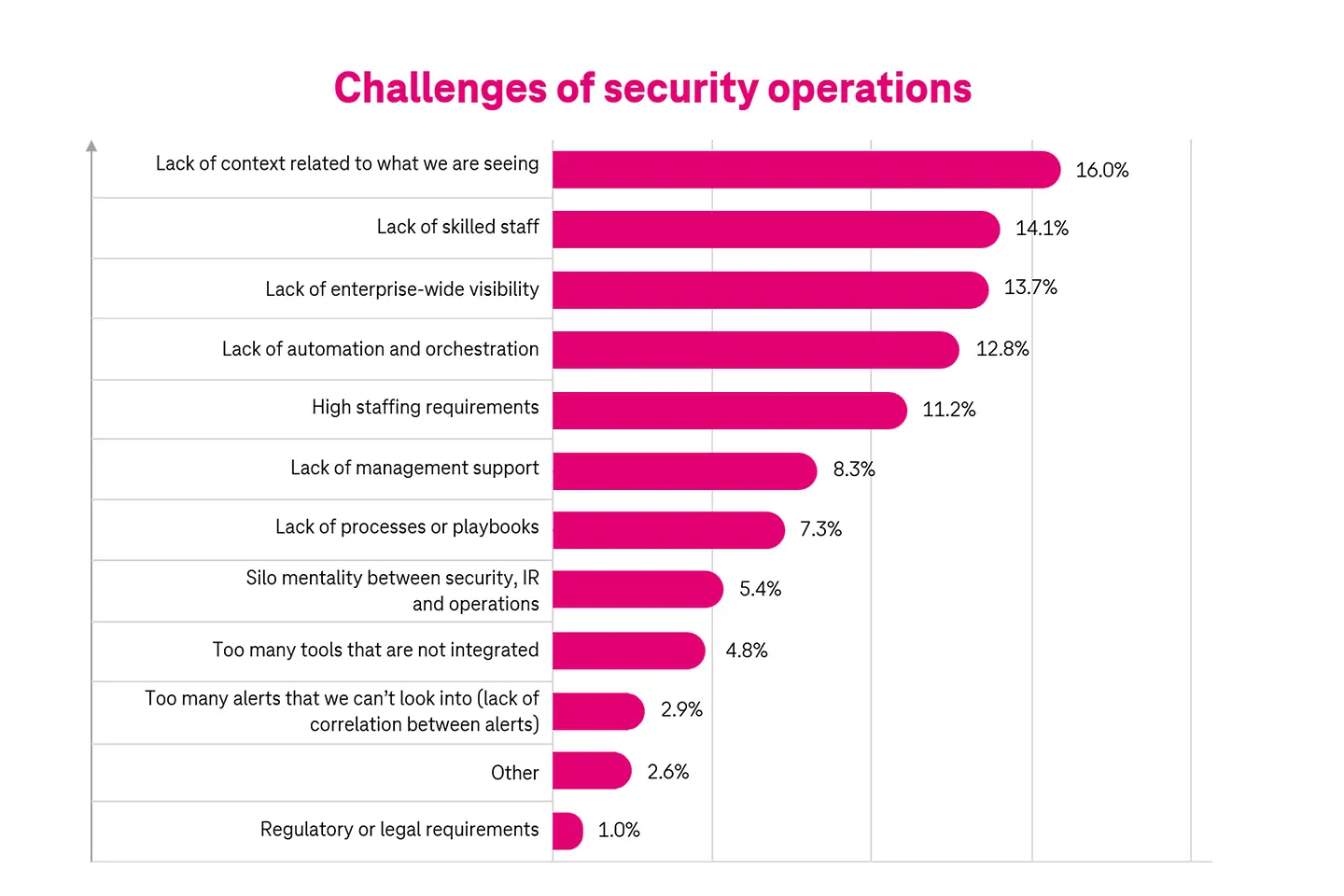
Here are some challenges of traditional SecOps1.
Modern SOCs are expected to deliver not just security, but also meet compliance, reporting, and training needs. With outdated security systems, security analysts face too many operational challenges. For instance, they’re always struggling to keep up with too many alerts.
In cyber security, context is king. The fundamental idea of setting up any security operation is to have threat intelligence capable of thwarting risks. However, there’s information overload, false alerts, and lack of context – this purpose of reducing risks is defeated. Additionally, these alerts overwhelm security analysts.
Analysts get thousands of alerts each day, here’s what a study2 found on average:
Such a flood of alerts is bound to put security analysts on the edge, so much so that 97% of them are worried about missing an alert when it’ll matter the most. That’s what happened with Target Corporation – a giant US-based retailer. In 2013, Target faced one of the largest data breaches where the credit and debit card information of about 41 million customers was stolen. This data breach cost the company $18.5 million in lawsuit settlement plus a bad reputation and a plunge in stock prices.
The real food for thought here is that alerts were raised by Target’s monitoring software (FireEye), but security experts chose to not act on them. Experts most likely ignored the alert as a false positive or a low-priority alert, like hundreds of others they receive daily.3
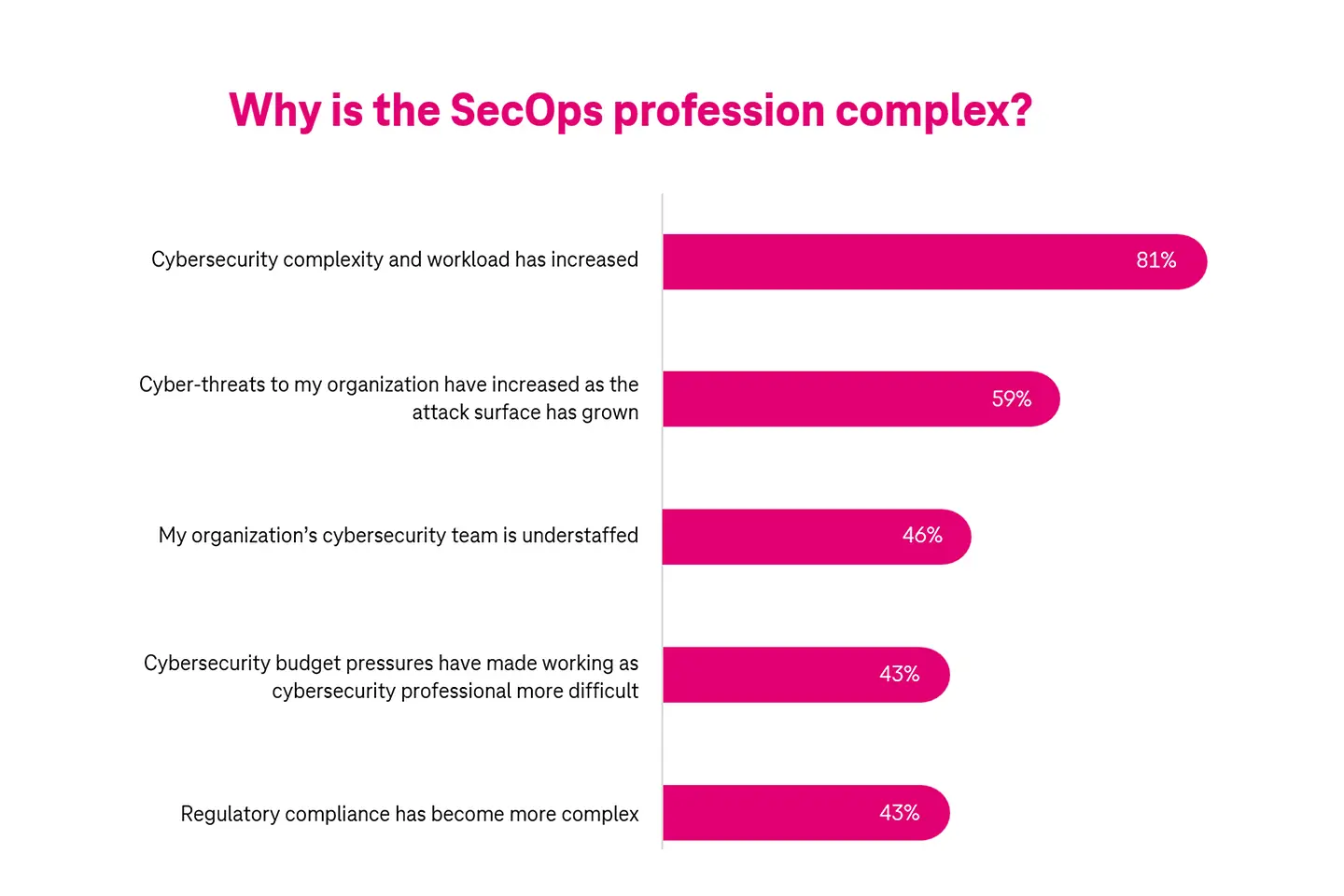
Too many alerts and very few security analysts to manage them is a big challenge. The root of this problem is in the manual dependency. A study in 2023 highlighted that about 81% of SecOps professionals feel manual investigation slows them down. They’re required to initiate remediation actions manually.4 The same study also indicated that the average time to detect and respond has increased in the last two years. Analysts spend about one-third of their daily time investigating threats that aren’t real.
The heart of the issue is the shortage of security professionals to manage operations at scale. The adoption of digital and cloud technologies has gone remarkably high, increasing the attack surface. However, the number of skilled professionals in the security domain hasn’t improved in the last two decades. Forbes reported that in 2023 alone there were 3.5 million jobs in cyber security to be filled. It takes about 150 days on average to fill a security vacancy.5 Security professionals feel that their jobs are more difficult than they were two years ago. That’s because of growing complexities, the ever-increasing attack surface, the constant need to train and upgrade, budget pressures, and stress on meeting regulatory compliance.6
With fewer human resources, the time taken to detect, analyze, and respond is higher. There are other challenges like scaling up operations, human errors in interpreting data, 24x7 hour monitoring, adaptability to rapid changes, etc. Skill shortage is one thing, but if human dependency is brought down, most of the problems relating to security operations can be solved. Automating operations and adding AI could help free up teams.
With a complex landscape, high volume of alerts, and speed of attacks – it’s impossible for organizations to completely rely on traditional security means. Modern SecOps should be equipped to recognize patterns, respond in real time, derive the right context, take care of compliance, and so on. About 63% of SOC professionals feel that technologies like Artificial Intelligence and Automation (or simply put, ‘Intelligent Automation’) can improve response time by a higher degree.7

Traditional signature-based detection isn’t sufficient today because of its inability to detect new zero-day attacks and keep up with large volumes of malware. Artificial Intelligence can help the SecOps team to identify both known and unknown cyber risks, even in the absence of a signature. Artificial Intelligence uses machine learning (ML) algorithms to analyze a large amount of data to detect anomalies and patterns. Rule-based phishing detection is also a dated method as it cannot identify newer and unknown phishing emails. Whereas AI analyzes the email structure, content, and user interaction to flag a potential phishing attempt.
The same goes for log analysis, AI-based security log analysis can handle huge volumes in real-time as compared to rule-based systems. Not just external threats, but any internal threats such as unauthorized access or suspicious data transfer can be flagged by the AI.
AI also makes network security very effective as its algorithms can monitor networks, detect unusual traffic patterns, identify unauthorized or suspicious devices on the network, etc. Businesses can effectively prevent data breaches and security incidents with Artificial Intelligence. A key feature of AI is that it keeps learning and improving over time. As new cyber threats get into the market, AI models can learn from the new data to put up even stronger defenses. Businesses using MDR services that have AI-based endpoint protection experience faster and more effective responses from the security teams. To summarize, AI helps SecOps to improve efficiency, enhance real-time detection, add scalability, increase accuracy in decision-making, and more.
AI frees up security teams from laborious tasks. It allows them to focus on tasks that are more critical and complex. With intelligent automation, important tasks like vulnerability scanning, patch management, threat detection, and incident response can be streamlined. AI also recommends actions and aids security teams in remediation. Organizations using AI can benefit from the rapid processing of data from diverse sources, recognizing patterns, and flagging cyber threats in real time. They’ve saved about 108 days in data breach response time as compared to organizations that didn’t invest in AI.8
As repetitive tasks are streamlined, the need for frequent manual intervention can be significantly brought down. The need for ‘additional’ human resources for routine tasks is reduced or even eliminated. Furthermore, with accurate threat intelligence – security analysts need not waste too much time investigating false positives. By improving the detection rates, resources can be utilized in important tasks.
As the response time to incidents is reduced, major attacks, data breaches, ransomware, etc. can be avoided – which can otherwise cause financial losses, regulatory fines, lawsuit claims, reputational damages, etc.
To understand the success of security operations after deploying AI, organizations need to keep tabs on these metrics:
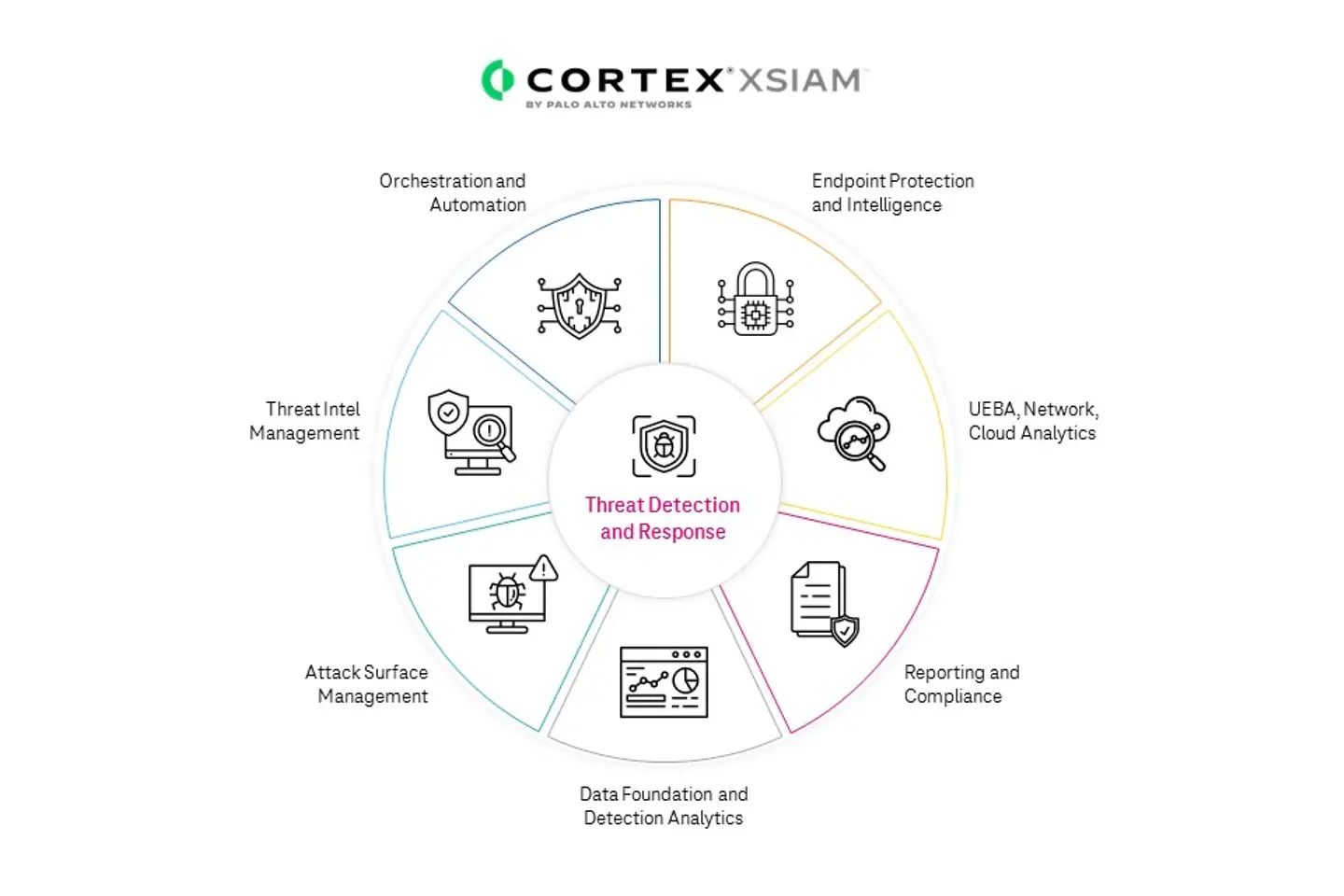
With our full-fledged MDR services, we help businesses improve SecOps, lower security risks, and increase business resilience without affecting their digital transformation journey. Our MDR services use new-age AI-based technology like Palo Alto Networks’ CORTEX XSIAM. With AI capabilities, we can ingest data from more sources, correlate different alerts better, and lower the volume of high-priority alerts. This, in turn, brings down the resolution time from days to minutes. The unnecessary time spent on investigating low-priority or false positive alerts is eliminated.
Palo Alto Networks’ XSIAM capabilities:
T-Systems and Palo Alto Networks can augment your existing security operations without needing huge investments in security tools and having to rejig the entire SOC. Enhance your organization’s security posture and improve cyber resilience to defend against modern-day cyber-attacks.
With our AI-based MDR services, you can:
To ramp up your security operations or benefit from our MDR services to build strong security for your business, get in touch with us now.
1 SANS 2023 SOC Survey, 2023, Medium
2 Security Alert Article, Help Net, 2023, Security
3 Target Data Breach Case Study, 2023, Card Connect
4 Global SOC Study Results, 2023, IBM
5 Cybersecurity Skills Gap, 2023, Forbes
6 The Life and Times of Cybersecurity Professionals, 2023, Enterprise Strategy Group
7 Global SOC Study Results, 2023, IBM
8, 9 Costs of Data Breach Report, 2023, IBM