
Even in today's cloud era, every resource, be it an EC2 instance, a VPC Lambda deployment, an API Gateway, or a RDS Database, needs to be accessible somehow. Oftentimes, access is made outside the VPC hosting the resource, or the component itself must connect to peered networks. IP address harmonization is frequently required. Amazon’s IPAM provides network administrators and sysadmins with an automated IP management workflow, lowering their management and monitoring burden.

AWS announced the Amazon VPC IP Address Manager (IPAM) service at its annual re:Invent event in Las Vegas in 2021. IPAM is designed to overcome the limitations of spreadsheet-based, homegrown IP planning applications and replace highly specialized and expensive IP address management solutions.
With IPAM, it is possible to organize company IP address spaces according to routing, security, and business rules. And with AWS IPAM's API actions, it is easy to reduce the time to onboard new applications from hours to a few seconds. AWS IPAM can be deployed to AWS Organisations and provides detailed monitoring of the IP addresses used, where, and when for up to three years.
Managing Bring your own IP addresses (BYOIP) public IP address spaces is also possible.
IT departments must provide as much user functionality as possible to their application teams while keeping technical solutions and security under control.
In large enterprises, it’s no longer possible to do IP address management manually. Traditional IP planning applications contain custom, complex logic without the necessary abstractions to provide API access for users. This restriction often results in provisioning processes where a designed solution must request IP address spaces from specific IT departments. Consequently, there is no possibility to create a self-service functionality for projects, and the time to set up the environment is unreasonably long.
One of our customers uses AWS Direct Connect, a dedicated network connection for its on-premise corporate networks. The networking area consists of shared VPCs used by multiple customers, with the option to isolate workloads in dedicated subnets and VPCs, and central VPCs, like egress VPCs. The network area spans across multiple regions. Managing the dedicated VPCs is delegated to specific system teams.
A common scenario is workloads that require a connection from or to on-premise setups and need to use IP addresses that are harmonized with the on-premise corporate network. Over time, the AWS environment has grown and now consists of multiple CIDRs between the size of /16 and /19, associated with multiple VPCs.
Additionally, private IP address spaces that are not harmonized are used for resources that do not need to communicate with the on-premise network.
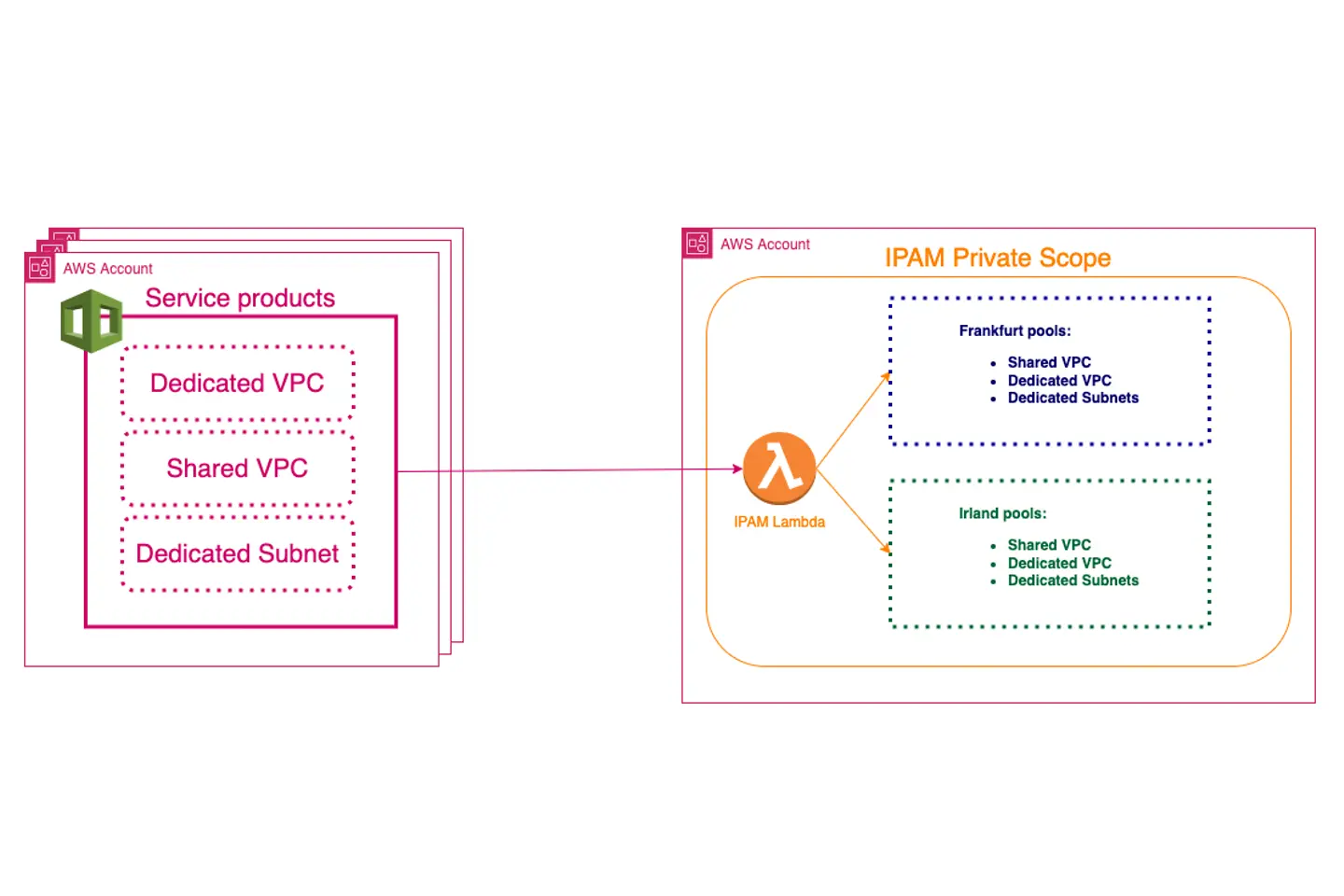
We used the AWS Service Catalog as the frontend to provide a user-self-service functionality. The catalog relies on CloudFormation as the infrastructure as code (IaC) solution, which we frequently implement.
We created the following IP pools, using IPAM locales to define top-level pools or assign pools to regions.
Private Scope:
IPAM is deployed into a separate AWS account. Currently, the only available native integration into IPAM is the VPC integration, where it is possible to define the requested IP pool and the necessary size of the network (netmask length).
As we also need to support dedicated subnets, we decided to create Lambda functions in front of IPAM. These functions are via CloudFormation custom resources. Here is an example:
Resource
GetCnCIDR:
Type: Custom::GetCnCIDR
Properties:
ServiceToken: !Ref IpamFunctionArn
Description: !Join ['', [!Ref 'AWS::AccountId', ' - vpc - ', !Ref VpcNamePrefix, '-', !Ref VpcCounter]]
CnCidrMask: !Ref CnCidrMask
DeleteCnCIDR:
Type: Custom::DeleteCnCIDR
Properties:
Authorizationkey: !Ref CustomerAuthorizationKey
IpamPoolAllocationId: !GetAtt GetCnCIDR.Returned_IpamPoolAllocationId
Cidr: !GetAtt GetCnCIDR.Cidr
CreationDate: !GetAtt GetCnCIDR.CreationDate
ServiceToken: !Ref IpamFunctionArn
To support the CloudFormation delete operation to work, we have to request the allocation ID while creating the stack. For the deletion, the release_ipam_pool_allocation method is required.
AWS Lambda resource-based policies protect the access to call our Lambda functions.
"IPAM provides a unified operational view and enables you to manage IP addresses across AWS Regions and your accounts."
Amazon, December 1. 2021
With AWS IPAM, it is easy to replace spreadsheet-based IP CIDR allocations, enable self-service networking, and provide insights into the resources using IP address spaces across multiple accounts and applications. Organizations can manage IP addresses globally, cross-region, cross-account, and also for non-AWS workloads.