
With the OT-IT convergence in manufacturing, the automotive sector also faces security risks. Major automakers in recent years have fallen victim to cyber attacks, leading to operational downtime, systems going offline, and ransomware payments. In this blog, find out how automotive companies can protect their production through security measures. Also read what global automakers are up to.
The convergence of operational technology (OT) and IT is not new. This close integration has helped most industries, such as manufacturing, energy and utilities, oil and gas, automotive, among others, to weed out efficiencies and improve decision-making. For example, many industrial and manufacturing organizations today use sensor data and advanced analytics together to predict equipment failure. Such predictive maintenance reduces downtime, improves asset performance, and increases equipment life. With these gains, organizations are spending to bring OT-IT even closer and scale digital transformation initiatives. The market for OT-IT is growing and expected to surpass USD 1 trillion by 2030. In 2023, it was USD 720 billion.1
As the Industry 4.0 phenomenon with smart manufacturing is getting widely adopted, the use of supervisory control and data acquisition (SCADA) systems is also rising. SCADA is a key system to monitor and control industrial operations, connecting OT-IT systems. A report suggests that its global market is set to reach USD 31.4 billion by 2034, from USD 10.5 billion in 2024, indicating a rise of 11.5% CAGR.2
Like most industrial organizations, the automotive industry has embraced the OT-IT integration well. For instance, major German automotive player, BMW, has tightly integrated OT-IT through its Industry 4.0 transformation. The company has integrated robotics and virtual reality with digital twins, cloud computing, and artificial intelligence (AI).
At its facilities such as Regensburg and Spartanburg, virtual reality (VR) is employed for production planning, employee training, and ergonomic assessments. Meanwhile, humanoid robots are being tested on repetitive tasks to enhance both efficiency and safety.
These innovations align with BMW’s iFACTORY vision and support the development of the Neue Klasse platform – their next-generation electric vehicle architecture centered on electrification, digitalization, and sustainability.
By combining real-time OT data with IT-driven simulations and analytics, BMW is optimizing production cycles, reducing planning time, and enabling faster, more stable vehicle launches. This OT-IT synergy is driving automation and innovation, setting new standards for connected, efficient, and human-friendly manufacturing environments.3
Modern production systems in automotive are no longer just machines; they integrate the internet of things (IoT) devices, software applications, cloud connectivity, digital twins, and much more. More automotive companies are integrating IoT components to enable automation, quality control, improve production cycles, and do much more. The global automotive IoT market, which was close to USD 142.8 billion in 2024, should surpass USD 1197 billion in 2034. That’s a CAGR of more than 23%..4
General Motors (GM), a US-based automaker, is also leveraging AI capabilities to predict and resolve maintenance-related issues. The automaker has integrated IoT sensors across its production facilities to collect real-time machine data. This data is analyzed using AI models to forecast potential equipment failures, enabling proactive maintenance and eventually resulting in significant cost savings with 15% lower unplanned downtime.5
Besides IoT, even the global automotive software and electronics market is growing at 5.5% CAGR and will reach USD 462 billion by 2030.6
Many automotive companies are making investments to ramp up capabilities around software, electric vehicles (EVs), and autonomous capabilities. South Korean automaker, Hyundai Motor Company (the third largest in the world by production capacity), is investing more than USD 16 billion to upgrade and modernize its production and launch modern vehicles, and a significant chunk of the budget is earmarked for building software capability.7
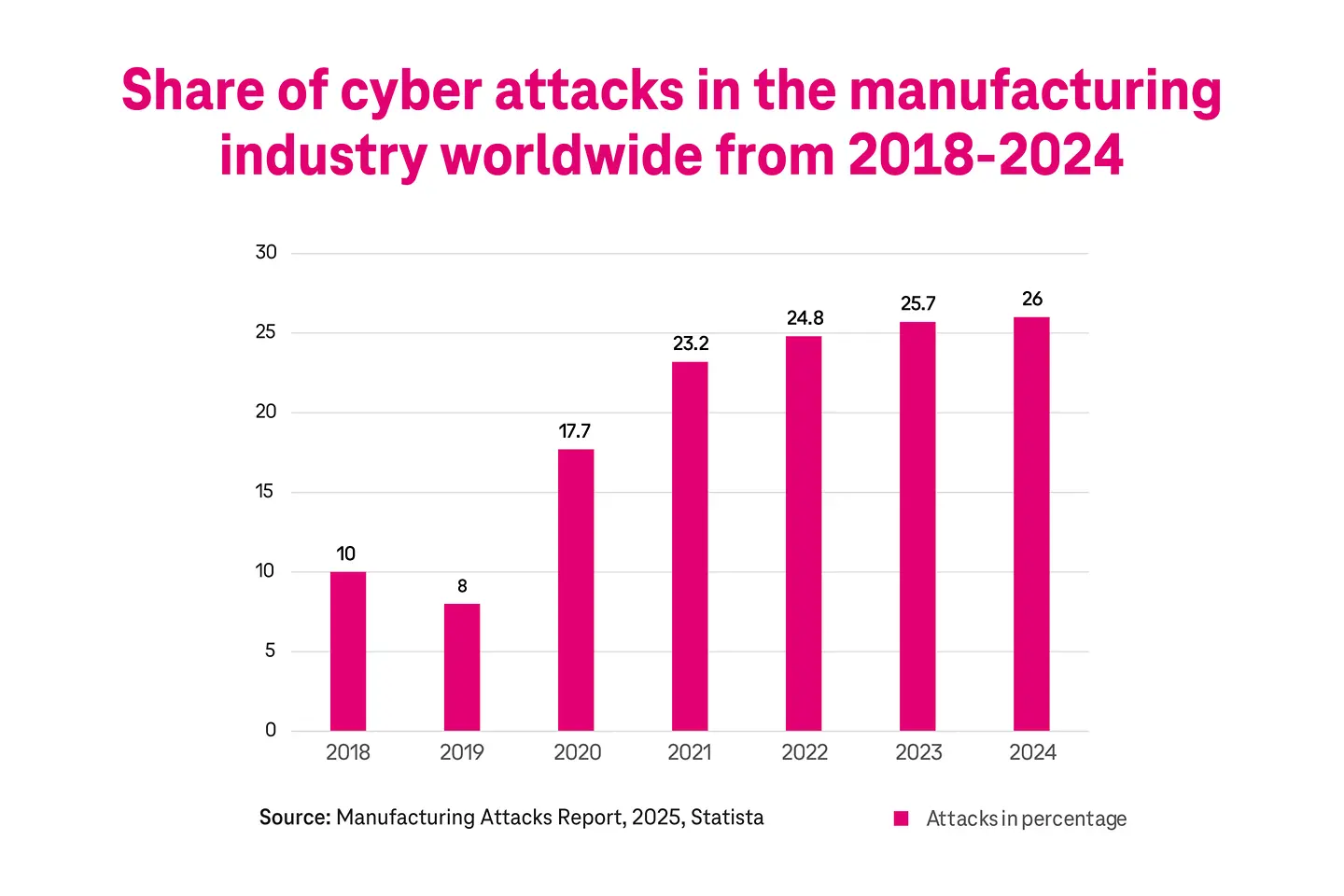
These numbers signify the fast-changing face of the automotive manufacturing industry. As more software goes into the vehicles, the automotive production systems also need to adapt. The integration of multiple technologies, as mentioned earlier, exposes the automotive industry to more security risks. As connected machines, IoT sensors, devices, and cloud applications are networked across the IT and OT layers, the attack surface increases. Any vulnerability in these systems could become a potential entry point for cyber criminals, leading to a cyber attack. In fact, manufacturing is one of the most targeted industries, accounting for one in every four cyber attacks.
Legacy systems (SCADA components/industrial control systems) in manufacturing plants often lack updates, strong authentication, or segmentation, often leading to cyber incidents. Many automotive firms have poor patch management in place, leading to downtime, which can turn out to be quite expensive. Every minute of downtime causes an average loss of USD 22,000 to manufacturers, which could sum up to USD 50 billion a year for industrial manufacturers.8
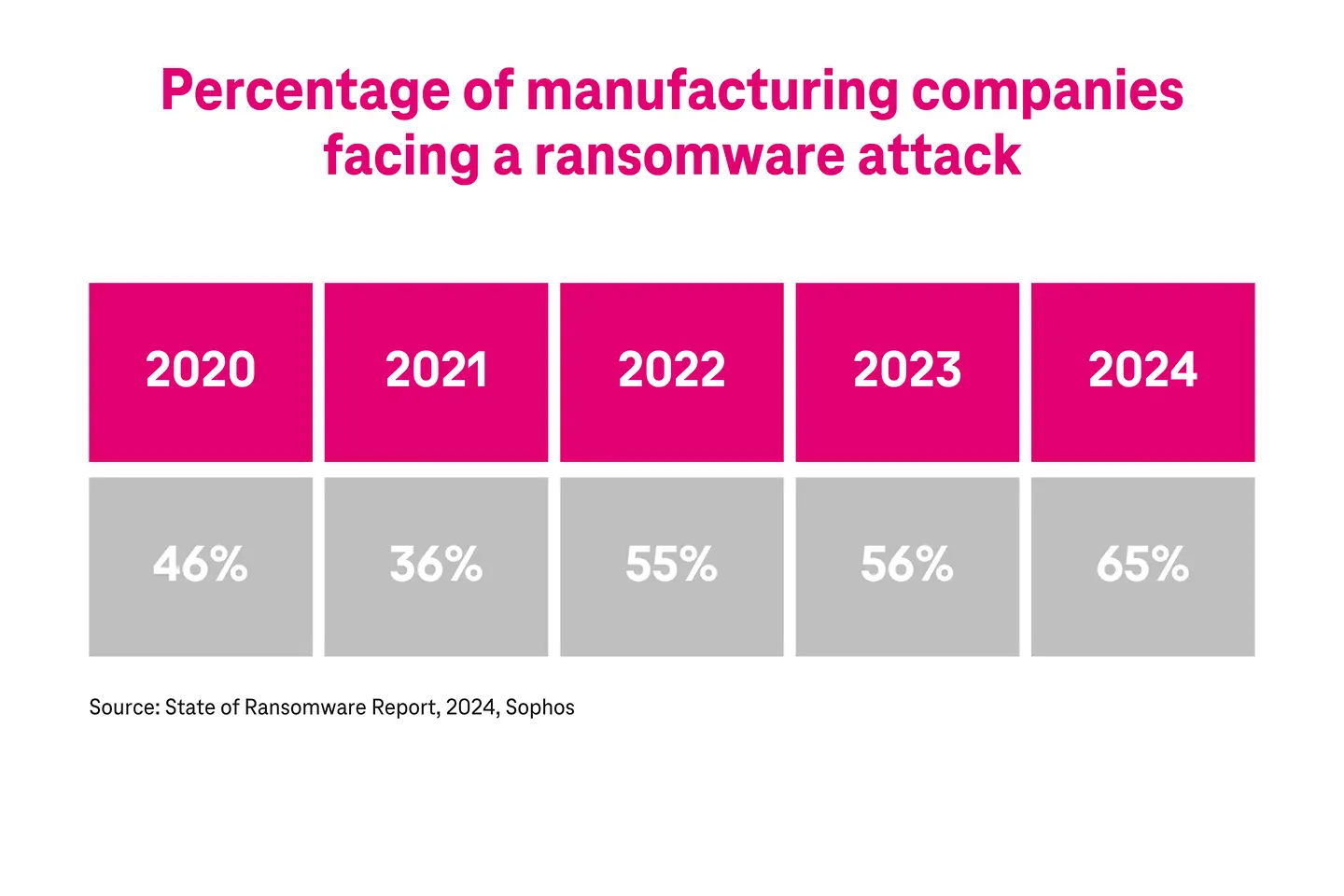
65% of manufacturing companies were targeted with a ransomware attack in 2025.10
In June 2020, Japanese auto brand Honda was targeted by the EKANS (Snake) ransomware, a strain designed to disrupt industrial control systems (ICS). The attack was highly targeted, with the malware containing hardcoded internal Honda domain names and IP addresses. It likely entered through an exposed remote access point, allowing attackers to deploy the ransomware manually.
EKANS terminated critical ICS processes, encrypted systems, and isolated them via firewall changes. As a result, Honda had to shut down production across multiple global facilities, including in Japan, North America, and Europe.
Although no data exfiltration was confirmed and no ransom was paid, the attack caused significant operational disruption, highlighting the risks of IT-OT convergence and the need for robust network segmentation and threat detection. This attack would have most likely cost Honda at least some millions of dollars due to production disruption. But the company has not disclosed any amount yet.9
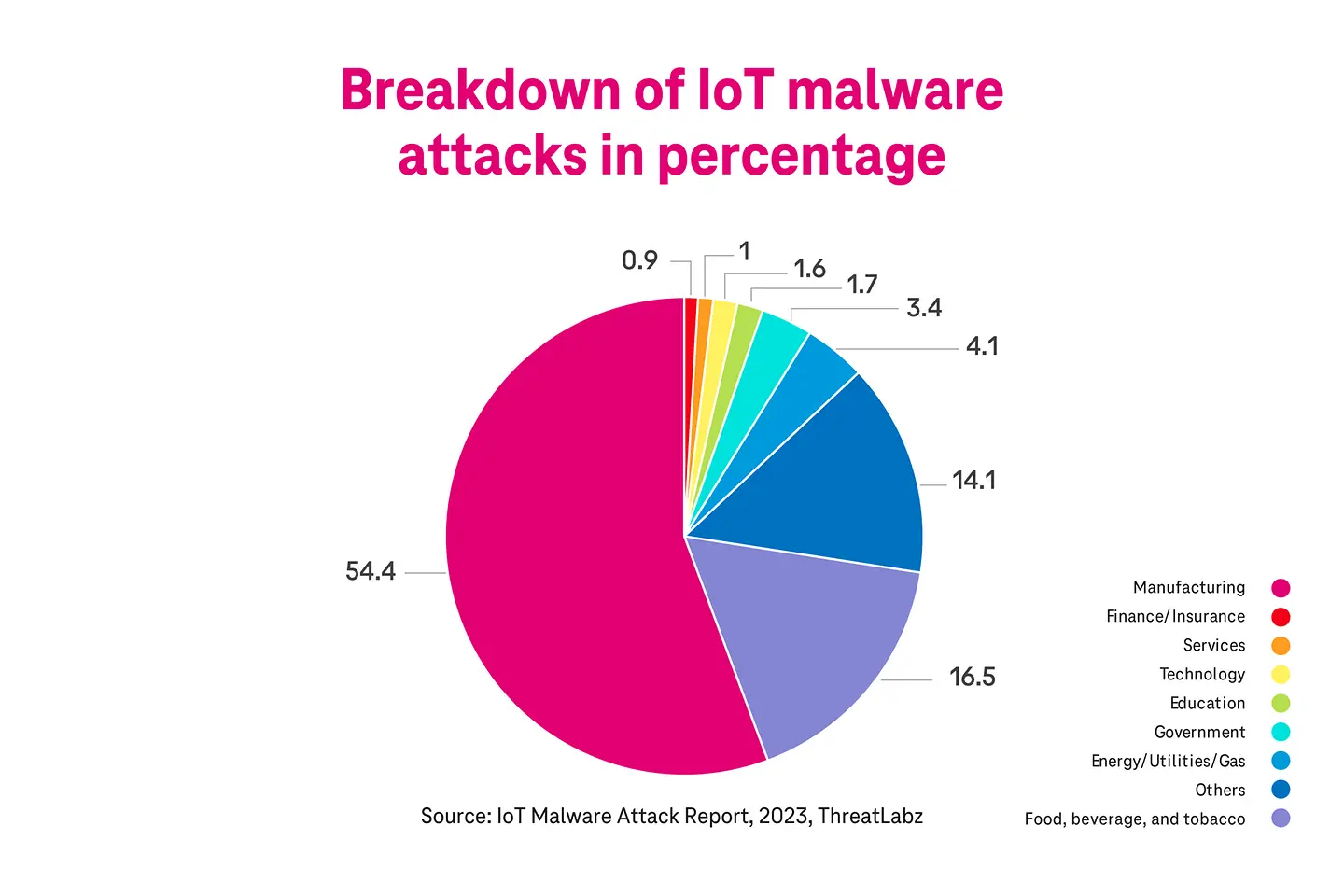
There are several other attributes that can become the causes of security incidents, such as IoT sensors and devices lacking security protocols. IoT-based cyber attacks have been increasing. The ThreatLabz report suggested that there was a 400% growth in IoT malware attacks, and the manufacturing sector suffers the most because the industry uses IoT devices the most. Here’s the breakdown of IoT malware attacks.11
Manufacturing setups, especially automotive, rely on a deep supply chain and multiple vendors. Often, a weak link in the supply chain can result in cyber attacks, and about 67% of automotive attacks can be attributed to suppliers.12
Imagine a software used by hundreds of auto dealers that gets infected with malware, causing operational disruptions and downtime for all the organizations relying on it. Might sound like fiction, but such incidents have occurred.
The CDK Global ransomware attack severely disrupted US auto dealerships by crippling the company’s core dealer management systems (DMS), which thousands of dealerships rely on for sales, inventory, and financing operations. The attack, attributed to the BlackSuit ransomware group, which exploited vulnerabilities in CDK’s internal systems via phishing or compromised credentials and encrypted critical infrastructure.
As a result, over 15,000 dealerships experienced outages, halting vehicle sales, service appointments, and customer transactions. CDK had to shut down systems for days, initiate a staged recovery, and reportedly negotiate with the attackers. The breach exposed how centralized IT platforms in automotive retail are single points of failure, pushing the industry to reevaluate third-party vendor risk, implement stricter access controls, and bolster incident response readiness.13
With more cloud connectivity, SCADA, programmable logic controllers (PLCs), and remote access tools, attacks are getting remote. In fact, remote attacks happen to account for more than 90% of the cyber incidents in automotive.14
For instance, an attacker exploits a vulnerability in a supplier's remote access virtual private network (VPN) used for maintenance. Once in, they move laterally through the flat network to reach the factory’s PLCs and SCADA systems, disrupt robot operations, and halt production, all without setting foot on site.
A weak security posture is often bad news and results in operational setbacks, downtime, bad press, escalating costs often in millions, and regulatory and compliance hurdles. To avoid these consequences, automotive companies must invest in security measures.
Microsegmentation works by dividing networks into smaller, isolated zones and enforcing granular access controls between them. In an automotive manufacturing environment, it prevents attackers who breach one system, such as a supplier-connected workstation or a test robot, from moving laterally into critical OT zones such as PLCs or SCADA systems. This containment reduces the blast radius of any breach and aligns with the principle of least privilege.
In the Honda ransomware attack mentioned earlier, if segmentation had been enabled, the impact of the attack would have been far lower. Isolating IT and OT systems would have prevented the spread of the malware in the production systems, limiting disruption to core manufacturing systems and allowing operations to continue in unaffected zones.
Secure access service edge or SASE integrates networking and security into a cloud-native service. It protects remote users and factory sites with consistent policies. Within SASE, zero trust network access (ZTNA) ensures that no device or user is trusted by default, even if it is inside the network perimeter. For automotive plants that rely on remote diagnostics, vendor maintenance, or cloud-connected production systems, SASE ensures secure, authenticated access with real-time inspection and logging.
Penetration testing simulates real-world attacks to uncover exploitable weaknesses in both IT and OT systems. Manufacturers can identify risks such as open ports on robot controllers or misconfigured remote access services. Regular red-team exercises test the resilience of not only systems, but also processes and personnel, improving the overall security posture.
Vulnerability management is essential for tracking, prioritizing, and remediating software flaws in production environments. Given the long lifecycle of manufacturing equipment and software, an effective vulnerability management program ensures timely patching of both legacy OT systems and modern cloud applications, reducing entry points for attackers.
If most IoT-based attacks are targeted towards manufacturing, imagine how vulnerability management and penetration testing can identify security flaws and allow manufacturers to fix them. Some automakers rely on external help to find security bugs and vulnerabilities in their systems. Japanese auto giant Toyota has collaborated with HackerOne to identify and fix vulnerabilities in its systems (Toyota and Lexus systems).
The program is designed to strengthen cyber security by identifying flaws in web apps, application programming interface (APIs), and backend systems before attackers can exploit them. The program has helped Toyota fix serious issues, such as an API flaw that exposed internal supplier systems, thereby preventing potential breaches.
Device security and encryption protect endpoints such as human-machine interfaces (HMIs), engineering laptops, and IoT sensors. In automotive factories where connected devices are abundant, full-disk encryption, secure boot, and firmware integrity checks ensure that even if devices are stolen or compromised, critical data and control paths remain protected.
Anomaly detection systems use machine learning to monitor network traffic and system behavior for deviations from normal patterns. In automotive production, it’s critical to detect unusual commands sent to a robotic arm or unexpected data flows between OT and IT systems. Fast detection stops attacks before they escalate.
OT security assessments evaluate the unique architecture, devices, and risks in operational environments. These assessments identify insecure protocols, unpatched firmware, and a lack of segmentation that could expose manufacturing processes. They also ensure alignment with industry standards such as ISA/IEC 62443, providing a roadmap for securing production systems.
Another critical layer is backup and recovery. Automotive manufacturers should implement immutable, segmented backups, stored in offline or secure vaults, to enable rapid restoration in case of ransomware or system wipeouts. Without reliable recovery, even a small breach can lead to major production delays. Strong data backups can reduce the cost of ransom in most cases, removing the leverage from the bad actors. Backups also allow organizations to maintain business continuity.
Together, these security measures form a multilayered defense for modern automotive manufacturing. As production environments grow more connected and data-driven, a unified strategy that bridges IT and OT is essential to ensure resilience and business continuity.
T-Systems can help you fix and build a strong security posture, improve resilience, and meet regulatory norms through its decades of experience in serving leading automotive brands across Europe and the globe. With over 4,000 automotive and security experts, and 15+ security operations centers (SOCs), we secure OT and IT architecture so that you can reduce cyber attacks, their impact, and eventually build compliant systems.
To understand which security solutions will fit your automotive systems the best, get in touch with us today.
1 IT-OT Convergence Themes, 2024, IoT Analytics
2 SCADA Market Size, 2025, Precedence Research
3 BMW & Industry 4.0 Article, 2024, Technology Magazine
4 Global IoT Market Report, 2025, Market US
5 General Motors & AI Article, 2024, Orgevo Consulting
6 Automotive Software and Electronics Market, 2023, McKinsey Company
7 Hyundai Motor Investment Article, 2025, Domain B
8 Costs of Unplanned Downtime, 2022, Forbes
9 Ransomware Attack on Honda, 2023, Control Engineering
10 State of Ransomware in Manufacturing, 2024, Sophos
11 ThreatLabz Report, 2023, Zscaler
12 Automotive Cyber Security Statistics, 2025, Market US
13 Global Auto DMS Hack Article, 2024, CACM
14 Automotive & Smart Mobility - Cyber Security Report, 2025, Upstream